
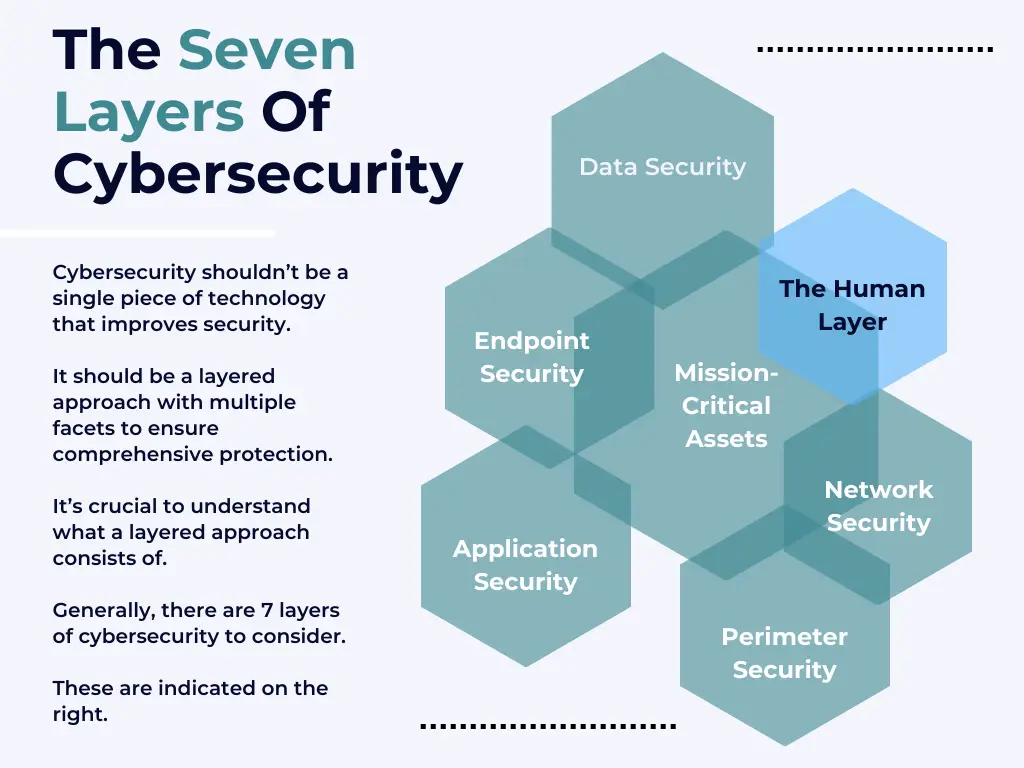
Welcome to the definitive Wlan Labs cybersecurity terms 101 hub. In a broad sense, cybersecurity is the practice of protecting electronic information from unauthorized access or theft. It encompasses a wide range of activities, from developing secure software to managing firewalls and intrusion detection systems.
The ultimate goal of cybersecurity is to protect sensitive data and prevent disruptions to critical infrastructure.
The need for cybersecurity has grown in recent years as the world has become increasingly reliant on technology. With the advent of the Internet of Things, more and more devices are connected to the internet, making them potential targets for cyber attacks.
In addition, the amount of sensitive data being stored electronically has skyrocketed, making it an attractive target for hackers. As a result, businesses and governments alike have invested heavily in cybersecurity measures in order to protect their assets.
Why Create This Cybersecurity Terms Hub?
It’s no secret that cybersecurity is a complex topic. With so many terms, attack types, and regulations to learn, it can be difficult to know where to start.
Cybersecurity is a critical part of protecting your digital life and your business. Without understanding the basics of cybersecurity, you’re putting yourself and your data at risk.
We’ve created this comprehensive guide to help you get started with cybersecurity. In addition to an overview of important terms and definitions, we’ve also included actionable steps that will help you learn more about this vital topic.
A
Active Directory Federation Service (AD FS)
Active Directory Federation Services (ADFS) is a software component developed by Microsoft to provide an organisation’s identity federation and single sign-on capabilities.
ADFS allows an organization to federate its Active Directory with other organizations, such as partners or customers, to provide a seamless user experience. For example, suppose an employee of Organization A needs to access a resource on Organization B’s network. In that case, ADFS can be used to authenticate the user and give them access to the resource.
Active Directory Security
Active Directory Security is a set of security features that are typically used to secure Windows networks. Active Directory Security can be used to control access to network resources, restrict what users can do, and monitor activity on the network. Active Directory Security is a comprehensive security solution that includes server-side and client-side components.
Active Directory Security is based on the principle of least privilege, which means that users should only have the minimum level of access necessary to perform their job duties. This helps to reduce the chances of accidental or unauthorized data loss or modification. Active Directory Security also includes Separation of Duties (SoD) controls, which help to prevent one individual from having too much control over a system.
Advanced Endpoint Protection (AEP)
AEP is a term for endpoint security software that defends a computer against malware by incorporating multiple layers of protection. These can include file reputation monitoring, exploit prevention, and behaviour-based detection.
AEP software is typically sold as a subscription service, and vendors often offer different levels of protection depending on the customer’s needs. For example, a small business might need protection against basic threats like viruses and spyware, while an enterprise might require more sophisticated security measures to protect against complex attacks.

Advanced Persistent Threat (APT)
An Advanced Persistent Threat (APT) is a type of cyber attack that is aimed at stealing information or disrupting operations. The goal of an APT is to gain access to a network and remain undetected for as long as possible.
State-sponsored hackers or criminal organizations often carry out APTs, and they can be challenging to detect and defend. Organizations should have robust security measures in place and be prepared to respond quickly if an APT is launched against them.
Adware
Adware is malicious software that hides on your computer and displays pop-up ads or other intrusive commercials when you are online. It can be difficult to remove once it is installed, and it can track your online activity to target you with even more annoying ads. Some adware programs may also install spyware or other types of malware on your system.
Attack Surface Management
Attack Surface Management reduces the risk that a malicious attack will succeed by reducing the number of potential entry points for an attacker.
It does this by identifying and assessing all potential points of vulnerability in an organization’s IT infrastructure and then taking steps to close as many of those vulnerabilities as possible. Attack Surface Management is essential for organizations that rely on information systems to conduct their business operations. Any successful attack against those systems could have a devastating impact on the Organization’s ability to function.
B
Backporting
Backporting is the practice of taking fixes and features from a newer version of the software and porting them into an older version. This is often done to maintain compatibility with older systems or provide new features and security updates to users of older versions.
Backporting can be a controversial practice, as it can introduce new risks and vulnerabilities to an old system. However, when done correctly and carefully, it can be valuable to keep old systems up-to-date and secure.
Botnet
A botnet is a network of compromised devices that carry out malicious activities such as distributed denial of service (DDoS) attacks, spam campaigns, or installing Ransomware. The devices in a botnet can be anything from home routers and smart TVs to smartphones and computers.
The botnet owner can rent out access to the compromised devices to other criminals looking to carry out nefarious activities. This makes botnets a powerful and dangerous tool for criminals and has resulted in billions of dollars in damages.

Brute Force Attacks
A brute force attack is a method of defeating a security system by trying every possible combination of passwords or keys until the correct one is found. Brute force attacks are often used to gain unauthorized access to systems or data and are especially common against weaker passwords.
There are many ways to protect against brute force attacks, including using strong passwords, limiting the number of login attempts, and using password/keyword-based authentication systems.
Bring Your Own Device (BYOD)
Bring Your Own Device (BYOD) is a policy whereby employees can bring their mobile devices, such as smartphones or tablets, into the office and use them to access corporate networks and data.
The idea behind BYOD is that it can save companies money on hardware because employees are already paying for the devices themselves. It can also improve employee productivity by allowing them to use the devices they’re most comfortable with. However, there are also security risks associated with BYOD, so companies need to put policies and procedures in place to protect their networks and data.
C
Cloud Access Security Broker (CASB)
A Cloud Access Security Broker (CASB) is a security solution that sits between an organization and their cloud service providers, providing enhanced security controls for the Organization.
A CASB can provide various security services such as:
- Identity and access management
- Data loss prevention
- Malware detection,
- Web filtering
- Granular policy enforcement
By sitting in between the Organization and their cloud service providers, a CASB can provide visibility and control over the Organization’s cloud services. This increased visibility and control can help to ensure that the Organization’s data is safe and secure when using cloud services.
Cloud Application Security
Cloud application security protects cloud applications from unauthorized access, use, disclosure, modification, or destruction.
Cloud application security is a critical consideration for organizations moving to or having already moved to the cloud. While cloud providers have implemented extensive security measures to protect their infrastructure and data, it is incumbent on organizations that use cloud applications also to take steps to protect their data and ensure compliance with applicable regulations.
There are several ways that organizations can secure their cloud applications, including adopting comprehensive security policies and procedures, encrypting sensitive data, deploying firewalls and other network security devices, and using identity and access management solutions.
Cloud Encryption
Cloud encryption is the process of transforming readable data into an unreadable format to protect it from unauthorized access.
The process of cloud encryption involves converting data into an unreadable format by adding a cryptographic key. This key is used to unlock the data and make it readable again. Without the key, the data remains unreadable, making it safe from unauthorized access.
Cloud Infrastructure Entitlement Management (CIEM)
Cloud Infrastructure Entitlement Management (CIEM) is the process of managing and regulating access to cloud infrastructure resources. This usually involves creating and maintaining a central repository of user entitlements, defining appropriate access levels for different users, and ensuring that only authorized users have access to the resources they need.
CIEM is a vital component of any cloud security strategy, as it helps to ensure that only authorized users can access sensitive data and systems. By implementing CIEM, organizations can help to prevent unauthorized access to their data and systems and safeguard their assets against potential threats.
Cloud Security
Cloud security protects data, applications, and infrastructure that are stored or accessed via the internet. It’s a broad topic covering a wide range of concerns, from ensuring data privacy to protecting against cyber attacks.
Organizations that use cloud services must consider both the security risks inherent in the technology itself and the potential for user error. In most cases, securing data in the cloud lies with both the provider and the customer. To protect your Organization’s data adequately, you need to understand and implement effective security measures at all layers of your cloud computing environment.
Cloud Security Architecture
Cloud security architecture is the overall system design encompassing all aspects of securing a cloud computing environment. It includes both the hardware and software components and the policies and procedures used to protect data and systems.
Cloud security architecture aims to provide a secure platform for storing, processing, and accessing data in the cloud. All system components must work together to protect data from unauthorized access or modification. The first step in designing a cloud security architecture is identifying the assets that need to be protected. These can include physical and virtual resources, such as servers, storage devices, networks, and applications.
Cloud Security Assessment
A cloud security assessment evaluates the security of an organization’s cloud infrastructure and identifies potential vulnerabilities. A cloud security assessment aims to identify ways that an attacker could exploit the Organization’s cloud resources and access sensitive data or systems.
Cloud security assessments can be performed in-house or by a third party assessor. In-house inspections are typically performed by a team of IT professionals familiar with the Organization’s cloud infrastructure. Third-party assessments are usually performed by a group of experts who have experience assessing the security of cloud infrastructures.
Cloud Security Posture Management (CSPM)
Cloud Security Posture Management (CSPM) is a cloud security technique that helps organizations assess and improve their security posture in the cloud. CSPM uses a combination of automated and manual processes to check for potential problems in an organization’s cloud configuration, identify security risks, and recommend remediation steps.
Although CSPM is primarily focused on improving an organization’s security posture, it can also help with compliance management and incident response. CSPM can help organizations avoid costly breaches or disruptions by identifying potential security issues early on.
Cloud Workload Protection (CWP)
Cloud Workload Protection (CWP) is the process of protecting workloads in a cloud environment. More specifically, CWP involves protecting data, applications, and infrastructures in a cloud environment.
There are many different ways to protect workloads in a cloud environment.
Some of the most common methods include:
- Data backup and replication,
- Application load balancing and failover
- Infrastructure redundancy
Each of these methods has its benefits and drawbacks. Data backup and replication are popular because they are relatively affordable and can be easily automated. However, it can be challenging to restore data from a backup if there is an outage.
Cloud-Native Application Protection Platform (CNAPP)
Cloud-native application protection platforms are systems that provide security for cloud-native applications. They offer automated policy enforcement, real-time activity monitoring, and runtime protection against attacks.
Cloud-native applications are those that are designed to run in the cloud. They typically use microservices architecture and can be deployed and scaled quickly and easily. Because they are intended for the cloud, they can take advantage of the scalability and elasticity of the cloud environment. However, they also present new security challenges, so cloud-native application protection platforms are needed.
Compromise Assessments
A compromise assessment analyses whether or not a systems security has been breached. This type of assessment is usually performed by third-party security experts without prior knowledge of the system. A compromise assessment aims to determine how attackers gained access to the system and what they did once they had access.
Container Security
There is no single answer to this question as container security is a broad and complex topic. However, container security refers to the security of containers used for storing and transporting data or applications. This can include both the physical security of the containers themselves and the security of the data or applications stored inside them.
Several different threats need to be considered when securing containers, and the most effective security measures will vary depending on the specific threats an organization faces.
Credential Stuffing
Credential stuffing is a cyberattack that uses stolen login credentials to access accounts or systems fraudulently. The term usually refers to attacks that use usernames and passwords from data breaches but can also include attacks that use credential theft tools, such as keyloggers and phishing scams.
Credential stuffing can be used to commit various crimes, such as identity theft, fraud, and stealing proprietary information. It can also be used to launch other types of cyberattacks, such as denial-of-service (DoS) attacks and malware infections.
Cross-Site Scripting (XSS)
Cross-site scripting (XSS) is a type of computer security vulnerability that allows an attacker to inject malicious code into a web page, resulting in code execution by unsuspecting users who visit the page.
XSS attacks can be used to steal cookies, passwords, or other sensitive data; or perform actions on the user’s behalf, such as logging them into a site without their knowledge. Cross-site scripting is one of the most common attacks against web applications.
Crypto-Malware
Crypto-malware is malicious software that uses cryptography to hide its tracks and payload. This makes it difficult for security researchers and victims to detect and decode the malware. Crypto-malware has been used in many high-profile attacks, such as the WannaCry ransomware attack that affected hundreds of thousands of computers worldwide.
Cryptojacking
Cryptojacking is a type of cybersecurity attack in which hackers infiltrate a victim’s computer and use its resources to mine cryptocurrency. This can be done by installing malicious software on the victim’s machine or persuading the victim to click on a malicious link.
Cryptojacking can result in significant financial losses for victims. Additionally, cryptojacking can be used to support other criminal activities such as money laundering and fraud. There are a number of ways to protect yourself from cryptojacking attacks, including ensuring that your antivirus software is up-to-date and refraining from clicking on links from unknown sources.
Cyber Espionage
Cyber espionage is obtaining confidential information from a company or Organization by unauthorized means. Typically, this is done by hackers who gain access to an organization’s network and then leverage that access to steal sensitive data. In some cases, cyber espionage may also involve social engineering techniques such as phishing or pretexting to trick employees into revealing confidential information.
Cyber espionage is a serious threat to businesses and organizations of all sizes. Hackers who can successfully carry out an attack can gain access to valuable trade secrets, customer data, and other sensitive information. This can give them a significant competitive advantage and harm the victim organization in many ways.
Cyber Kill Chain
The cyber kill chain is a vast and multi-layered concept in cybersecurity. It reflects the various stages that an attack can take, from initial reconnaissance to post-compromise activity and data exfiltration.
Understanding the kill chain aims to anticipate and thwart attacks at any stage. This requires a comprehensive Security Operations Centre (SOC), which watches for malicious activity across people, processes and technology at every layer of the stack.
Lockheed Martin first described the kill chain in 2011 as part of their work on detecting and preventing Advanced Persistent Threats (APT).
Cyberattack
A cyberattack is an attempt by a person, group, or nation-state to penetrate or damage a computer network or system.
Cyberattacks can be carried out in many ways, including malware infection, denial-of-service attacks, and data theft. They are often used to access confidential data, launch extortion campaigns, or sabotage critical infrastructure.
Cybersecurity
Cybersecurity is the practice of protecting your computer networks and user data from unauthorized access or theft. This can be achieved through various methods, including using firewalls, installing antivirus software, and creating strong passwords.
It’s essential to keep your computer networks and user data safe from cybercriminals, as they can use this information to steal your identity, money, or other sensitive data. Cybersecurity is therefore of paramount importance for businesses and individuals alike.
D
Dark Web
The dark web is a subset of the deep web. The deep web refers to all of the content on the internet that is not indexed by search engines, such as content behind paywalls, password-protected pages, and pages that are not crawled due to slow connection speeds or other technical reasons.
The dark web, estimated to be 5% of the entire internet, refers specifically to websites and content that can only be accessed through special software such as Tor, I2P, and Freenet. This software allows users to surf the internet anonymously and prevents their activities from being tracked. The dark web is often associated with illegal activities such as drug trafficking, arms smuggling, and human trafficking.
Dark Web Monitoring
Dark web monitoring is the process of tracking, monitoring, and analyzing data found on the “dark web” – the hidden part of the internet that’s only accessible using special software.
This data can include everything from stolen credit card numbers and login credentials to sensitive personal information. These days, more and more businesses are being targeted by cybercriminals – so it’s essential to have a proactive approach to security. That’s where dark web monitoring comes in.
When you monitor the dark web, you’re essentially checking out for any sensitive information that may have been leaked about your company or employees. This can help you mitigate risk and avoid costly damage control in a data breach.
Data Exfiltration
Data exfiltration is the unauthorized removal of data from a computer system. It can be done manually, by a malicious insider, or remotely by an attacker who has gained access to the system. Data exfiltration can also be accidental when an employee copies sensitive data to a personal device or account.
There are many ways to exfiltrate data, including copying it to removable media, emailing it outside the Organization, or uploading it to a cloud storage service. Data exfiltration can be used to steal trade secrets, personal information (such as medical records), or other sensitive information. Data exfiltration is challenging to detect and prevent because it often uses legitimate channels and tools.
Data Loss Prevention (DLP)
Data loss prevention (DLP) is a term used in the cybersecurity industry to refer to tools and processes designed to stop sensitive data from being lost or stolen. Predominantly, this involves preventing unauthorized users from accessing or copying confidential information, but it can also include ensuring that data is adequately backed up and protected against malware attacks.
DLP solutions typically work by monitoring network traffic and identifying sensitive data as it flows through the system. This data can then be blocked from being transferred to unauthorized locations or encrypted to protect it from being read by unauthorized users. In some cases, DLP systems can also generate alerts if sensitive data appears to be at risk of being lost or stolen.
Defense in Depth (DiD)
Defense in depth (DiD) is a security strategy that aims to protect an organization’s computer systems by using multiple layers of security controls.
These controls can include:
- Firewalls
- Intrusion detection/prevention systems
- Antivirus software
- Locked doors
By using multiple layers of security, an organization can reduce the risk that a single vulnerability will allow an attacker to gain access to its systems. For example, if an attacker succeeded in breaching the firewall, they would still be confronted with several other layers of defense before they could access sensitive data or applications.
Denial-of-Service (DoS) Attacks
Denial-of-service (DoS) attacks are a type of cyberattack where the attacker attempts to disrupt or disable a computing or network resource. The most common type of DoS attack is a flooding attack, in which the attacker sends large amounts of data or traffic to the target resource in an attempt to overwhelm it and cause it to crash or become unavailable.
Other types of DoS attacks can include attacks that exploit vulnerabilities in the target software or system, denial-of-service amplification attacks, and malicious botnets. DoS attacks can significantly impact businesses and organizations, as they can result in lost productivity, revenue, and customers.
DevSecOps (Development, Security and Operations)
DevSecOps is a term that emerged in the cybersecurity community to describe the practice of integrating security into the software development process. The idea is to move away from traditional, reactive approaches to security and instead build security into the very fabric of the software development process.
In DevSecOps, developers and operations teams work hand-in-hand with security professionals to build security into every stage of the software development cycle, from coding and testing all the way through to deployment and monitoring.
Digital Forensics and Incident Response (DFIR)
Digital forensics and incident response (DFIR) is the process of detecting, responding to, and investigating digital incidents. DFIR encompasses a variety of activities, including data collection, analysis, identification, preservation, and presentation.
The goal of DFIR is to help organizations mitigate threats and protect their data. DFIR teams typically include individuals with expertise in cybersecurity, information technology (IT), law enforcement, and forensics.
Distributed Denial-of-Service (DDoS) Attacks
A DDoS attack is a type of cyber attack that aims to disrupt the regular operation of a computer or network by overwhelming it with service requests. The system is no longer able to handle them all. This is achieved either by disrupting the hardware or overwhelming the network’s capacity.
DDoS attacks are usually carried out by botnets, which are networks of computers infected with malware that allow attackers to control them remotely.
By using multiple computers in a DDoS attack, the attacker can generate a much larger volume of traffic than would be possible from a single computer. DDoS attacks can have many different goals, such as preventing users from accessing a website or taking down a server.
Domain Spoofing
Domain spoofing is a technique cybercriminals use to to impersonate a website or online service fraudulently. By taking over the DNS (Domain Name System) records for a domain, attackers can redirect users to illegitimate websites or services or collect their personal information.
Domain spoofing can also be used to phish users into revealing their login credentials and other sensitive information. To protect themselves from domain spoofing attacks, users should always ensure that they visit the correct website by checking its URL and SSL certificate. They should also be careful about entering their personal information into any web form, even if it appears to be legitimate.
E
Email Encryption
Email encryption is the process of transforming readable email using an algorithm into unreadable text. This is done to protect email messages from being read by anyone other than the intended recipient.
Email encryption can be used in conjunction with other security measures, such as authentication and message integrity checking, to provide enhanced protection for email communications.
There are a variety of email encryption algorithms that can be used, including Pretty Good Privacy (PGP) and Secure/Multipurpose Internet Mail Extensions (S/MIME).
When these algorithms are used with appropriate software, they can provide effective protection against most forms of email-based attacks, including eavesdropping, message tampering, and unauthorized access.
Email Encryption Services
Email encryption services protect email communications from being read by anyone other than the intended recipient. This involves transforming readable email messages into unreadable ciphers using a key, which someone with the corresponding key can only decrypt.
Email encryption services can protect the privacy of email communications and ensure that email messages cannot be tampered with or forged. They are typically used by businesses and organizations to protect confidential information and individuals to protect their privacy.
Email Security
There are a number of aspects to email security. Still, in general, it can be thought of as any measure taken to protect email messages from being read or altered by unauthorized individuals.
This includes both the transmission of email messages (i.e. ensuring that they are properly encrypted and not susceptible to interception) as well as the storage of email messages (i.e. making sure that they are stored securely and only accessible to authorized users).
Email Spoofing
Email spoofing is a type of attack that tricks an email recipient into thinking that a message came from someone other than the actual sender. Email spoofing can trick people into revealing confidential information or spread viruses and other malware.
Email spoofing is accomplished by forging the “From” address in an email message. The “From” address can be falsified to make it appear as if the message was sent from another email address or even from a legitimate company or Organization. This can be done either by modifying the email headers before sending the message or by using a spoofing service that creates fake email addresses.
Endpoint
An endpoint is a network device, such as a computer, laptop, smartphone or tablet, that is used to connect to a network. In cybersecurity, an endpoint refers to a device used to access sensitive data or systems. Attackers can target endpoints to gain access to valuable corporate data or systems.
As such, cybersecurity teams often take measures to secure endpoints, such as mandating security software and encryption. In recent years, the Bring Your Own Device (BYOD) trend has led to an increase in attacks on corporate endpoints because personal devices are often less secure than corporate ones.
Endpoint Detection and Response (EDR)
Endpoint detection and response (EDR) is security software that helps protect computers and networks from malware and other threats. EDR software works by monitoring activity on a computer or network for signs of malicious activity. If suspicious activity is detected, the software can take action to block it, such as shutting down access to the machine or network.
EDR systems can also generate reports that detail the suspicious activity, which can help security analysts investigate and understand attacks. EDR systems are often used in conjunction with antivirus and firewalls to provide an additional layer of protection.
Endpoint Management
Endpoint management in cybersecurity identifies, responds to, and mitigates security risks posed by endpoint devices such as laptops, smartphones, and other connected devices.
It encompasses both physical and logical security controls, including features like firewalls, encryption, Access Control Lists (ACLs), application whitelisting and more. Endpoint management aims to protect the data and systems housed on an endpoint device from unauthorized access or theft while also ensuring that authorized users have the necessary level of access to perform their job functions.
Endpoint Protection Platforms (EPP)
An endpoint protection platform (EPP) is security software that helps protect individual devices, such as computers, laptops, and smartphones, from malware and other threats. It can also allow employees to access corporate resources securely and remotely.
An EPP usually consists of two main components: an anti-malware engine and a firewall.
- The anti-malware engine scans incoming traffic for threats and blocks them if necessary.
- The firewall prevents unauthorized users from gaining access to a network or device.
Endpoint protection platforms are often used with other security measures, such as firewalls, intrusion detection/prevention systems (IDS/IPS), and email and web filtering.
Endpoint Protection Software
In cybersecurity, endpoint protection software is an application that helps protect devices on a network from malicious activity. It does this by scanning for and blocking threats before they can do damage. Some endpoint protection software also includes features that allow users to remotely wipe or lock down devices if they are lost or stolen.
Endpoint protection software is an essential part of any organization’s cybersecurity strategy, as it can help mitigate the risks posed by malware, Ransomware, and other types of online threats. When choosing an endpoint protection solution, it’s important to consider your Organization’s specific needs and find one that offers robust security features and ease of use.
Endpoint Security
Endpoint security is the term used to describe the security measures taken to protect individual devices connected to a network, such as laptops, PCs, smartphones and tablets. Endpoint security includes antivirus and anti-malware software, firewalls, intrusion detection and prevention systems (IDS/IPS), and data loss prevention (DLP) technologies.
Today, organizations face many cyber threats, making it more important than ever to have robust endpoint security. With so many different types of devices accessing corporate networks, it can be challenging to keep track of them and ensure they are all properly secured.
Ethical Hacker
There are many different types of hackers, but the term “ethical hacker” refers to someone who uses their hacking skills for good rather than evil. Ethical hackers are also sometimes called “white hat hackers.” They use their skills to find security flaws in systems and help companies fix those problems before malicious hackers can exploit them.
One helpful way to think of ethical hacking is a security checkpoint. Just like how an airline checks luggage for potential threats before it’s allowed on a plane, ethical hackers probe a company’s digital defenses to look for weaknesses that could be exploited.
F
File Integrity Monitoring
File integrity monitoring is regularly checking the files on a computer system to ensure that they have not been changed, damaged, or removed. This is often done by comparing the current state of the files against a known “good” state.
File integrity monitoring can be used to help protect against malware, ransomware, and other types of cyberattacks. It can also help ensure that data is not modified or deleted intentionally or accidentally.
Fileless Malware
Fileless malware is a type of malware that does not require a file to be stored on the target system to execute. Instead, fileless malware executes directly in the system’s memory, which makes it more difficult to detect and prevent.
One of the main evil benefits of using fileless malware is that it’s challenging to detect using traditional antivirus software. This is because conventional antivirus software relies on scanning files on a disk for signatures of known malware threats. However, since fileless malware lives solely in the system’s memory, it’s not possible to detect it using this method.
G
Graduated Security
Graduated security is implementing a more stringent security policy for users who have a higher level of access to sensitive data or systems. For example, a company might have a less strict security policy for employees who only need to access limited information and a more stringent security policy for employees who need to access confidential data or systems.
The idea behind graduated security is that users with greater access to sensitive data or systems pose a greater risk if they are compromised. By implementing a more stringent security policy for these users, the company can reduce the risk of a data breach.
H
Hacktivism
Hacktivism is a blend of the words “hack” and “activism” that refers to computer hacking techniques for political or social purposes. Hacktivism can be used for various ends, including disrupting systems or stealing data to publicize a cause or champion a cause. In some cases, hacktivism may also involve developing new software or hardware to advance a political agenda.
While the term “hacktivism” was only coined relatively recently, the concept has been around for much longer. Many famous hackers can be considered hacktivists throughout history, including the LovESHack group that protested against nuclear weapons in the 1980s and 1990s.
Honeypots
Honeypots are a type of security mechanism used in cybersecurity. They are computer systems set up to look like they are vulnerable to attack. In reality, they are not. This is done to lure potential attackers into coming onto the system to monitor and track their activity.
This information can then be used to help protect other systems on the network from being attacked. Honeypots can also be used for research purposes to learn more about how attackers operate and what methods they use.
Hybrid Cloud
A hybrid cloud is a cloud computing environment that uses a mix of on-premises, private cloud, and public cloud services. The goal of using a hybrid cloud in cybersecurity is to provide the best of both worlds—the flexibility and scalability of public clouds with the security and control of on-premises solutions.
There are several benefits to using a hybrid cloud in cybersecurity. One advantage is that it can help organizations improve their security posture. By combining the security features of on-premises solutions with the scale and flexibility of public clouds, organizations can better protect their data against cyber threats.
I
Identity Access Management (IAM)
Identity access management (IAM) defines and manages user access to systems and data. It includes provisioning and de-provisioning user accounts, setting and enforcing access control policies, and auditing user activity.
IAM is a critical component of cybersecurity efforts because it helps ensure that only authorized users have access to sensitive data and systems. By adequately configuring IAM, organizations can significantly reduce their risk of attack.
There are many different components to consider when implementing an IAM solution, but some of the most important include identity management, authorization, authentication, and auditing.
Identity Security
In the simplest terms, identity security in cybersecurity is safeguarding an individual’s online identity. This can be done in several ways, but the most common method is by ensuring that the individual’s personal information (such as their name, address, and Social Security number) is not compromised.
Additionally, identity security also involves protecting an individual’s online activity and transactions from being monitored or tampered with.
Identity Segmentation
Namely, Identity Segmentation is the creation of non-overlapping security segments within an organization, each with its own unique identity allowing for differentiated levels of security and access. This can be done at both network and host levels.
By compartmentalizing systems in this way, companies can limit the spread of damage in the event of a breach and make it easier to identify which systems are affected. Additionally, analysts recommend that multi-factor authentication (MFA) be implemented when possible to add an extra layer of security.
The most well-known example of how effective Identity Segmentation can be is the United States military’s use of compartments within its networks.
Incident Response (IR)
Incident response (IR) is the process of addressing and managing incidents. An incident, in this context, is an event that poses a potential threat to an organization’s information security. The goals of incident response are to minimize the damage caused by an incident and restore normal operations as quickly as possible.
Incident Response Steps
The first step in any incident response plan is to identify the incident. This may sound like a trivial step, but it’s often not easy to determine whether an event is genuinely an incident or just a random occurrence. Once the event has been identified, the following steps will depend on the type of incident and the Organization’s specific policies and procedures. However, some general steps are typically taken in most cases.
These steps might include preserving evidence, notifying appropriate personnel, containment and eradicating the threat, and post-incident analysis. Each of these steps is critical to minimizing damage and preventing further incidents.
Indicators of Compromise (IOC) Security
There are many indicators of compromise, or IOCs, in cybersecurity. Some common IOCs include:
- IP addresses associated with malware or attacks
- Domain names used by attackers
- URLs visited by victims before and during an attack
- Email addresses used to send phishing emails or malware
- Hashes of malicious files
- Personal information of employees or customers (such as names, email addresses, and credit card numbers) stolen in a breach
Each Organization will have different IOCs based on its structure, data, and systems. For example, an e-commerce website will likely have different IOCs than a hospital.
Infrastructure as a Service (IaaS)
IaaS is a type of cloud computing that provides users access to computing resources, such as servers and storage, over the internet. IaaS providers offer their customers the ability to rent a portion of their infrastructure or, in some cases, to use someone else’s infrastructure.
IaaS has become a popular choice for businesses that need to outsource their IT infrastructure. By using IaaS, companies can avoid the cost and complexity of deploying and managing their own IT infrastructure. IaaS providers manage the hardware and software for their customers, freeing businesses to focus on their core business functions.
Infrastructure as Code (IaC)
Infrastructure as Code (IaC) is the process of managing, provisioning and deploying computing infrastructure resources using software. IaC tools allow for the automated creation, deployment and configuration of resources in a repeatable manner. This can include compute instances, storage, networking and other related resources.
IaC is often used in conjunction with DevOps practices to help streamline the application development process. By using IaC tools, organizations can automate the build and deployment process for applications, reducing the time required to get new applications into production. IaC can also help improve security by automatically allowing organizations to enforce security policies on infrastructure resources.
Internet of Things (IoT) Security
The internet of things (IoT) is a term for the ever-growing network of interconnected devices that can interact with each other. This includes everything from smart thermostats and refrigerators to cars and medical devices. The security of these devices is a significant concern, as they could be vulnerable to cyberattacks that could potentially cause harm or even death.
There are several ways that IoT devices can be secured, including using strong passwords, updating software regularly, installing antivirus software, and using firewalls. It’s also important to be aware of the potential risks of using IoT devices and take appropriate precautions.
IOA vs IOC
The IOA (Input/Output Administration) and IOC (Input/Output Control) models are two different approaches to administering and controlling input/output operations in a cybersecurity system.
Historically, the IOA model has been more popular because it is more efficient and easier to manage. In this model, an administrator defines what type of input and output is allowed for each user, and then the system automatically enforces these rules.
However, the IOC model is gaining popularity because it is more flexible and adaptable. In this model, administrators define users’ desired input/output behavior, and the system then automatically adapts its operations to meet these objectives.
IT Security
IT security is a process of protecting your computer networks and user data from unauthorized access, use, disclosure, disruption, or destruction. IT security includes the practices and technologies that are used to protect your computers and data from unauthorized access or theft.
Some standard methods of IT security include firewalls, passwords, encryption, and antivirus software. Firewalls help to prevent unauthorized access to your computer networks by blocking incoming and outgoing traffic based on specific criteria.
Passwords help secure your user data by requiring authorized users to enter a password before accessing the data. Encryption helps protect your computer data from being accessed by unauthorized individuals by converting the data into an unreadable format.
J
K
Kerberos
Kerberos is a secure authentication protocol initially developed at MIT, allowing two entities to communicate over an insecure network without needing a third party.
Kerberos works by requiring each entity to possess a unique key called a “ticket”. Tickets are issued by an authorized Kerberos server (called a “ticket-granting service”) and can be used only by the entity for which they were issued.
When a client wants to connect to a server, it sends its ticket to the server and its user name and password. The server checks the ticket against its list of authorized tickets, and if everything matches up, it allows the client to connect.
L
Lateral Movement
Lateral movement is a term used in cybersecurity to describe moving from one compromised system to another to gain access to sensitive data or systems. This type of attack is typically carried out by attackers who have already gained a foothold on a network and are trying to expand their access. Lateral movement can be done using various techniques, such as Pass the Hash, social engineering, and exploit tools.
In many cases, lateral movement is executed using stolen credentials. Once an attacker has obtained these (usually through phishing), they can then use those credentials to move laterally throughout a network until they find the systems or data they’re looking for.
M
Malvertising
Malvertising is a type of online advertising that employs viruses, spyware, and other malicious code to infect computers and devices. Malicious ads are often used to spread malware or collect sensitive information like passwords and credit card numbers. These ads can be found on legitimate websites as well as shady ones. It’s important to be aware of malvertising and take steps to protect yourself from it.
There are a few different ways that malvertising can work. One is by simply displaying a pop-up ad that looks normal but contains malicious code. The code automatically runs and infects your computer or device when you click on the ad. Another way is by redirecting you to a malicious website after clicking on an ad.
Malware
Malware is a term used to describe malicious software, including viruses, worms, Trojan horses, and spyware. Malware can be installed on your computer without your knowledge or consent and can cause serious problems. It can hijack your web browser and redirect you to unwanted websites or steal personal information such as passwords and credit card numbers.
Malware can also slow down your computer’s performance or even prevent it from starting up. If you think you might have malware on your computer, it’s important to scan it with an antivirus program and remove any found infections.
Malware Analysis
Malware analysis is the process of identifying and characterizing malware to understand its purpose and functionality. This can be done to determine its threat level or develop defenses and countermeasures against it.
Various techniques can be used for malware analysis, including static and dynamic analysis. Static analysis involves examining the code of a program without actually executing it to infer its behavior. On the other hand, dynamic analysis involves running the program and observing its behavior as it executes.
Both static and dynamic analysis have their advantages and disadvantages. Static analysis is generally faster and easier to automate, but it can be less effective at uncovering some types of malware behavior.
Malware vs Virus
Malware and viruses are both very harmful to your computer. They can cause your computer to crash or give someone access to all of your personal information.
Malware is a type of software that is designed to harm or disable computers. It can be a virus, a Trojan horse, spyware, adware, or a worm. Viruses are also malware, but there are other types of malware. A virus is a malware that can self-replicate and spread from computer to computer.
Trojans are another type of virus that masquerades as legitimate software but do damage when you run them on your computer. Spyware collects information about you without your knowledge and sends it back to the hacker.
Man in the Middle (MITM) Attack
A Man in the Middle (MITM) attack is where an attacker inserts himself into communication between two parties to intercept and view or modify the exchanged information. In a MITM attack, the attacker uses his resources to impersonate one of the devices or systems involved in the original communication without either party being aware that a third party is involved.
As a result, all communications between the two original parties are routed through the attacker’s system.
There are many ways that an attacker can carry out a MITM attack. Still, some standard methods include using false DNS entries to redirect traffic to a malicious server, using arp poisoning to send false MAC addresses and redirecting traffic.
Managed Detection and Response (MDR)
Managed detection and response (MDR) is a subscription service that organizations can use to outsource their cybersecurity needs. This service provides access to a team of security experts who monitor an organization’s network 24/7/365 and take action if they detect any malicious activity.
MDR services can be highly beneficial for organizations that do not have the internal resources or expertise to manage their cybersecurity posture effectively. By partnering with an MDR provider, organizations can enjoy peace of mind knowing that their networks are constantly monitored and protected.
Additionally, MDR providers can often offer better pricing than comparable in-house solutions, making them more cost-effective for many businesses.
MITRE ATT&CK Framework
The Mitre ATT&CK framework is a cyber-threat intelligence gathering and analysis methodology. It provides a common language and taxonomy for discussing cyber-attacks and offers a structure for classifying attacks and threat actors.
The Mitre Corporation developed the framework in collaboration with the US Department of Defense. Furthermore, it is used by both private companies and government agencies as a standard tool for assessing and responding to cyber threats.
Mobile Malware
Mobile malware is malicious software designed to target mobile devices, such as smartphones and tablets. While the term can refer to any malicious software that targets mobile devices, it is most commonly used for malware designed to steal data from the device or infiltrate business networks through the device.
The prevalence of mobile devices and the fact that they are often used for sensitive activities, such as online banking and shopping, make them an attractive target for cybercriminals. In addition, many people do not take proper security precautions with their mobile devices, such as using strong passwords or installing security updates on time. This makes it easier for criminals to exploit vulnerabilities in these devices.
Multi-Factor Authentication
Multi-factor authentication (MFA) is an authentication method in which a user is required to present two or more pieces of evidence (or “factors”) to a secure system in order to gain access.
The most common type of MFA uses something you know (a password or PIN), something you have (a physical token or key), and something you are (biometrics). This is often referred to as 3-factor authentication. More advanced systems can use additional factors, such as location, time of day, or the specific device being used.
MFA is designed to overcome the weaknesses of single-factor authentication methods, such as passwords and PINs.
N
Network Security
Network security is a subset of cybersecurity that focuses on protecting the networks used by businesses and other organizations. These networks may include both local area networks (LANs), wide-area networks (WANs), wireless local networks (WLANs) and the associated devices, such as routers, switches, and firewalls.
Network Segmentation
Network segmentation is a security measure that involves dividing a computer network into smaller, more manageable parts to improve the security of the overall network. By separating the network into segments, it becomes more difficult for a hacker to gain access to all network parts should they penetrate one segment.
Each segment can be secured with unique security measures, including firewalls, antivirus software, and user authentication protocols. Additionally, limiting communication between components makes it more difficult for a hacker to move laterally through the network and access sensitive data.
Next-Generation Antivirus (NGAV)
It is a type of security software that uses various techniques to protect your computer from malware and other threats proactively.
NGAV systems are designed to supplement or replace traditional antivirus software, which has become less effective at protecting against new threats. NGAV products vary in their approach, but all attempt to address the issue of rapidly changing malware by using a combination of static and dynamic analysis to detect malicious code. This allows them to see both known and unknown threats, offering a more comprehensive level of protection than traditional antivirus software.
NTLM
NTLM stands for Network Transition Long-Standing mode and is a proprietary Microsoft security protocol. It authenticates and secures communications between clients and servers in a network environment. To understand NTLM, it’s important to understand the challenges it was designed to address.
One of the biggest challenges in networking is ensuring that communications are secure. When data is passing back and forth between different devices, there’s always the potential for someone to intercept it and either view or modify the data without permission. Consequently, any networking protocol needs to include some mechanisms for encryption and authentication.
O
One Time Pad (OTP)
One-time pad (OTP) is a type of encryption considered unbreakable. It uses a random key that is used only once to encode data. The key is never reused, so there is no way to decrypt the data without the original key. OTP is thought to be hacker-proof because even the slightest change in the ciphertext will result in a completely different encrypted text.
OTP is also known as the Vernam cipher, named after its creator Gilbert Vernam. He came up with the idea in 1917, but it wasn’t until 1919 that it was implemented. Both government and military organizations have used OTP for secure communications over unsecured channels.
Operations Security (OpSec)
Operations security (OpSec) is a process by which an organization protects its operational capabilities from exploitation, interference, and sabotage by internal and external threats. OpSec protects information that pertains to the planning and conduct of an organization’s operations.
One of the main objectives of OpSec is to prevent enemies from acquiring information about an organization’s intentions, capabilities, and activities. The goal is to make it difficult for enemies to piece together information about an organization, so they can’t figure out what it is doing or plans to do.
OpSec also includes protecting organizational assets from insider threats. This means protecting against employees or contractors who may try to steal or leak sensitive information for their gain.
Outside Threat
An outside threat refers to any malicious act or activity that is not initiated by an authorized user of a computer system or network. An unauthorized user may be an employee who has exceeded his or her authorized access or a hacker who has broken into the system from outside.
The term is often used to describe attacks by hackers, whether they are motivated by financial gain, espionage, revenge, or destruction. Cybercrime, in general, is becoming increasingly sophisticated and dangerous as more and more sensitive data is stored online. Protecting against outside threats is one of the most critical challenges for businesses and governments in the 21st century.
Over-The-Air (OTA)
Over-The-Air (OTA) refers to transferring data wirelessly from one device to another. This can be done either through an access point or directly between two devices. OTA is often used in cases where it is not possible or convenient to physically connect the devices, such as updating firmware or exchanging data between devices that are not in the same location.
One everyday use for OTA is updating firmware on Internet of Things (IoT) devices. Due to a large number of IoT devices and the complexities involved in managing them, it is often easier and more efficient to push updates out over the air rather than physically touch each device.
P
Patch Management
Patch management is installing software updates, also called patches, to improve the security of computer systems. By keeping systems up to date with the latest security patches, organizations can reduce their risk of being hacked.
Patch management is a critical part of any cybersecurity strategy. Still, it can be challenging to keep track of all the patches for all the different applications and operating systems used in an organization. That’s why it’s crucial to have a system in place for deploying patches quickly and efficiently. Patch management software can help automate this process, making it easier for organizations to stay updated with the latest security patches.
Penetration Testing
Penetration testing is the practice of exploiting vulnerabilities in systems or applications to determine if those vulnerabilities are exploitable.
The goal of penetration testing is to identify the vulnerabilities in a system so that they can be fixed and then conduct a simulated attack against the system to determine how well those fixes work. Penetration testing can also be used to test an organization’s cybersecurity readiness by simulating an attack against the Organization and seeing how well it can defend itself.
Phishing
Phishing is the process of attempted fraudulent activity using email, instant messaging, or malicious websites to deceive users into providing personal information such as login credentials or credit card details. Such data can then be used to steal the user’s identity or access their accounts and carry out criminal activities.
Phishing attacks are usually carried out by sending emails or instant messages that appear to come from a trusted source, such as a financial institution or online service provider. The message may contain links that take the user to a spoofed website that looks identical to the actual site but is actually under the attacker’s control.
Once on the fake site, the user may be tricked into entering their login credentials or other sensitive information. Phishing awareness training is something that companies of all sizes should consider to offset such threats.
Phishing Testing
Phishing testing is the process of assessing the susceptibility of an organization’s email users to phishing attacks.
Phishing tests are typically performed by sending emails that mimic real-world phishing attacks and then measuring how many users click on links or open attachments in the email.
Organizations can use phishing test results to refine their email security policies and procedures and educate employees about identifying and avoiding phishing scams.
Platform as a Service (PaaS)
Platform as a Service (PaaS) is a cloud computing platform for developing, testing, and deploying applications. It is a way for businesses to outsource the development and deployment of their applications.
In cybersecurity, PaaS can develop and deploy security applications and tools. It can also be used to test new security tools and applications before they are released into the market.
Principle of Least Privilege (POLP)
Principle of least privilege (POLP) is an important concept in cybersecurity that dictates that users should only have the level of access to systems and data that is necessary for them to do their jobs. This minimizes the risk of accidental or malicious abuse of privileges that could compromise sensitive information or damage critical systems.
For decades, the principle of least privilege has been a cornerstone of security best practices. Still, it has taken on new significance in recent years as organizations grapple with the challenges of protecting against increasingly sophisticated cyber attacks.
Q
Quarantine
Quarantine is a designated area on a computer or network where infected or potentially harmful files can be isolated and contained. This helps prevent the spread of infection and ultimately protects the rest of the network. In most cases, quarantines are implemented through software that monitors all activity on the network and automatically isolates any file or device that shows signs of being compromised.
R
Ransomware
Ransomware is malware that encrypts a victim’s files and then demands a ransom for the victim to regain access to their files. This type of malware has become increasingly common in recent years, with several high-profile ransomware attacks making headlines. While Ransomware can be used for malicious purposes, it can also be used as a tool for legitimate businesses, such as law firms, to protect their client data.
So what exactly is Ransomware? Ransomware is a form of malware that utilizes encryption to lock users out of their data unless they pay the attacker a ransom. The most common types of Ransomware are dormant until triggered by an action taken by the user.
Ransomware as a Service (RaaS)
Ransomware as a Service (RaaS) is a type of malicious software that allows cybercriminals to launch ransomware attacks without developing their own code or infrastructure. RaaS providers typically offer an affiliate program that will enable people to sign up and distribute the Ransomware in exchange for a cut of the ransom payments. This model has made it possible for anyone with basic computer skills to launch sophisticated ransomware attacks.
Since RaaS arrived on the scene, there has been a dramatic increase in ransomware attacks. Many companies and individuals have become victims of these attacks because they are often difficult to defend against and can result in significant losses.
Ransomware Detection
As mentioned above, Ransomware is a type of malicious software that threatens to publish a victim’s data or block access to it unless a ransom is paid. Ransomware detection identifies ransomware-related ‘anomalies’ in network traffic or system behaviour to take corrective action before any damage is done.
Traditional signature-based antivirus solutions are ineffective against Ransomware, as the malware rapidly evolves and mutates to avoid detection. However, some newer behavioral detection methods can be used to identify ransomware activity.
These include machine learning techniques that analyze ransomware behavior and automatically generate signatures for new variants and honeypots and sandboxes that can detect suspicious activity and fileless infections.
Ransomware Examples
Some ransomware examples are CryptoLocker, TeslaCrypt, and Locky. They are all very similar in that they encrypt your files and then demand a ransom payment to unlock them. Typically, ransom payment is demanded in Bitcoin or some other cryptocurrency.
Some people mistakenly believe that ransomware is a new phenomenon, but it has been around for some time. The first known ransomware attack happened in 1989 when an IBM employee named Joseph Popp sent out 20,000 infected floppy disks to random people. The disks would install a program that would encrypt the user’s files and then display a message demanding a $300 ransom payment.
Red Team VS Blue Team
In cybersecurity, Red Team vs Blue Team refers to the two main types of security teams. Red Teams are responsible for identifying and exploiting security vulnerabilities, while Blue Teams work to establish and maintain secure networks. Both teams play an essential role in ensuring the safety of digital systems and data.
Red teaming exercises typically involve simulated attacks carried out by experienced security professionals. These simulations help test an organization’s response to a real-world threat scenario. Blue Teams can improve their defenses against potential attacks by understanding how Red Teams operate.
Remote Desk Protocol (RDP)
Remote Desk Protocol (RDP) is a remote access protocol that allows a user to connect to a computer over a network. System administrators use it to manage their systems and by end-users to connect to their computers from anywhere. RDP is built into Windows and can be enabled on Mac and Linux systems using third-party software.
RDP is vulnerable to attack because it provides a wide range of privileges to the user. Attackers can use RDP attacks to take control of the target computer, steal data, or install malware. RDP attacks are one of the most common methods to breach corporate networks.
Risk-Based Vulnerability Management
Risk-Based Vulnerability Management (RBVM) is assessing risk and vulnerability to determine the most effective way to manage security threats. The goal is to identify and prioritize vulnerabilities to mitigate the most significant risk. This can be done by assessing the likelihood of a threat occurring, the potential impact if it does, and the cost of mitigating each vulnerability.
RBVM is a critical part of any cybersecurity strategy, as it allows organizations to focus their resources on the biggest risks. By identifying and addressing high-risk vulnerabilities, organizations can better protect themselves against cyberattacks and threats.
Rootkit Malware
Rootkit malware allows attackers to access and control your computer system without your knowledge or permission. Rootkit malware can enable someone to remotely take over your system, steal your data, or spy on you. It’s considered one of the most dangerous types of malware because it’s challenging to detect and remove.
Runtime Application Self-Protection (RASP)
Runtime Application Self-Protection (RASP) is an application security solution that protects applications from malicious actors while they are running in production. RASP inserts security controls into the application itself, allowing it to detect and respond to malicious activity in real-time.
Because RASP is embedded within the application, it can provide detailed insights into how the application is being used and react immediately to any malicious activity. This makes RASP a powerful tool for stopping attacks that would otherwise go undetected. Additionally, because RASP is implemented at the application level, it does not require any underlying infrastructure or codebase changes.
S
Scareware
Scareware is malware that attempts to trick users into believing their system is infected with a virus or other piece of malicious software. The goal of scareware is to convince users to purchase a fake antivirus program or other security product to “fix” the non-existent infection. In some cases, simply clicking on a pop-up ad can infect your computer with this type of malware.
Scareware is notoriously tricky to remove and often requires the assistance of a professional malware removal specialist. If you believe you may be infected with scareware, it’s important to avoid clicking any ads or pop-up windows and to run an antivirus scan as soon as possible.
Security as a Service (SECaaS)
Security as a Service (SECaaS) is a cloud-based security solution that enables businesses to outsource their security needs to a third party.
Businesses that opt for SECaaS can benefit from increased security and decreased costs and administrative overhead. By outsourcing their security needs, companies can focus on their core competencies and leave the task of maintaining a secure network infrastructure to the experts.
SECaaS providers offer a wide range of services, including firewalls, intrusion detection/prevention systems, antivirus/anti-malware protection, web filtering, etc. Many providers also provide 24/7 support so businesses can rest assured, knowing that their security is constantly being monitored.
Security Awareness Training Programs
Security awareness training programs are educational programs that teach employees about the importance of security and how to protect company data.
Topics typically covered in security awareness training programs include the following:
- The different types of cyberattacks and how to spot them
- How to protect your computer and online accounts from hackers
- How to keep your personal information safe online
- What to do if you suspect a data breach has occurred
Security Information and Event Management (SIEM)
Security Information and Event Management (SIEM) is a technology that aggregates and analyzes data from multiple security sources to provide real-time visibility into an organization’s security posture. SIEM system technologies typically include a centralized console, event correlation engine, and threat analytics capabilities.
The goal of SIEM is to help organizations more quickly identify, track, and resolve security incidents by providing visibility into all aspects of their IT environment. This can include everything from network activity and user activity to faults and events generated by applications and systems.
Security Operations Center (SOC)
A Security Operations Center (SOC) is a centralized unit that manages an organization’s security posture. A SOC team is responsible for identifying, responding to and neutralizing cyberthreats.
The main functions of a SOC team are to monitor network traffic and events, analyze vulnerabilities and incidents, and take corrective action to mitigate risks. A SOC team may also be responsible for developing and maintaining security policies and procedures and training staff on cybersecurity best practices.
In order to effectively carry out its mission, a SOC team must have access to the latest security tools and technologies. They must also be able to rapidly share information with other units within the Organization, such as the IT department or incident response team.
Security Orchestration, Automation and Response (SOAR)
Security Orchestration, Automation and Response (SOAR) is a cybersecurity platform that enables organizations to automate and streamline their security operations. SOAR provides a centralized console for managing security incidents, automates response processes, and integrates existing security tools and technologies.
It helps Security Operations Centers (SOCs) effectively respond to incidents by reducing the time it takes to discover, investigate, and resolve them. Additionally, SOAR can help recommend appropriate mitigations for future incidents based on its past analysis.
Shadow IT
Shadow IT refers to the use of information technology resources and applications without the knowledge or approval of the Organization’s IT department. In the context of cybersecurity, it can pose a serious risk to an organization’s network if these unauthorized applications and devices are not adequately secured.
Shadow IT is often the result of users seeking solutions to business problems when they feel that the official tools and processes are too slow or cumbersome. While this lack of patience can be frustrating for IT staff, it’s essential to understand that users typically have good intentions and are simply trying to be productive. The trouble with Shadow IT is that it bypasses all of the security controls that have been put in place by the Organization.
Shift Left Security
Shift Left Security is the term used for a security model that focuses on identifying and remediating vulnerabilities and risks earlier in the software development life cycle. Traditionally, security has been approached as an afterthought once the software or application is already developed and in use.
However, with Shift Left Security, security is integrated into the development process. This helps to ensure that vulnerabilities are identified and addressed early on before they have a chance to cause damage or be exploited.
Social Engineering Attacks
Social engineering attacks are a broad category of attacks that seek to exploit human weaknesses to obtain sensitive information or access systems. These attacks can take many different forms, but they all exploit our natural tendencies to trust others and follow social norms.
Common examples of social engineering attacks include phishing emails, phone scams, and tailgating (forcing one’s way into a secured area by following someone who has access). By tricking people into revealing confidential information or giving them unauthorized access to systems, attackers can wreak havoc on organizations of all sizes. As the world becomes more interconnected, social engineering attacks are only likely to become more common.
Spear-Phishing
Spear-phishing is a social engineering attack that targets a specific organization or individual rather than random victims. The attacker uses the information they’ve gathered about their target to create a more believable email message, hoping to trick the target into clicking on a malicious link or opening an infected attachment.
Spear-phishing attacks are often very successful since the victim is more likely to trust an email message if it looks like it’s coming from someone they know. And since the attacker has taken the time to learn about their target, they can create very realistic messages that are difficult to spot as scams.
Spearphishing vs Phishing vs Whaling
- Spearphishing is a type of phishing attack in which the attacker uses personal information to gain trust and then launches an attack. The attacker may use public information, such as social media profiles, to find information that can be used to personalize the attack. For example, they may send an email that appears to be from a trusted source, such as a work colleague or friend, that contains malware or asks for personal information.
- Whaling is a type of spearphishing attack that targets high-level individuals within an organization, such as executives or members of the Board of Directors. The attacker uses personal information to create a message that appears to be from a trusted source, such as the CEO or another executive and asks for sensitive information or approval for a fraudulent transaction.
- Phishing is a cyberattack that uses malicious emails or websites to trick people into giving personal information, such as passwords or credit card numbers. The attacker may pose as a trusted organization, such as a bank or online retailer, and send an email with a link to a spoofed website. The website may look legitimate but is actually designed to steal information. Phishing attacks can also occur through text messages and phone calls.
Spoofing Attacks
A spoofing attack is a type of cyberattack where the attacker impersonates another user or computer system to gain access to sensitive data or systems. The attacker can use various techniques to spoof their identities, such as IP address spoofing, email address spoofing, and website forgery.
Spoofing attacks are often used in conjunction with other types of attacks, such as phishing and social engineering, to trick victims into divulging sensitive information or downloading malicious software. However, even without these additional tricks, spoofed emails and websites can often fool innocent users into thinking they are dealing with a legitimate entity. Spoofing attacks can have severe consequences for both individuals and organizations.
Spyware
Spyware is a type of malware that performs malicious actions on a computer, such as spying on the user’s activities or stealing their personal information.
Spyware can be installed on a computer in several ways, including through infected websites, email attachments, and fake software updates. Once installed, it can collect confidential data such as usernames and passwords, credit card numbers, and other personal information. It can also track web browsing habits and record what websites are visited.
Spyware can pose a serious threat to your privacy and security, so it’s essential to keep your computer protected with antivirus and anti-spyware software.
SQL Injection
A SQL injection is an attack that uses input validation vulnerabilities to inject malicious SQL statements into an application. These statements can be used to steal data, execute commands on the server, or even compromise the entire database.
Because SQL is a common language used to query and manipulate databases, attackers often try to exploit vulnerabilities in applications that use SQL to gain access to sensitive data or take control of the server. Developers and users must be aware of these risks and take steps to protect their applications from such attacks.
Supply Chain Attack
A supply chain attack is an attack in which an attacker targets a weak point in a company’s supply chain to gain access to the company’s systems or data. A supply chain attack can be devastating to a company, as it can give the attacker complete control over its systems and data. The most common type of supply chain attack is a trojan horse attack, in which the attacker includes malicious code in a software update that is then distributed to the company’s customer base.
Supply chain attacks are becoming increasingly common, as they offer a quick and easy way for attackers to gain access to many companies at once. In addition, a large number of companies do not have adequate security measures in place to protect themselves.
T
Tailgating
Tailgating, also known as piggybacking, is a type of social engineering attack in which an attacker gains access to a secured area or facility by following another person who has already been granted access.
While tailgating can technically be carried out in any type of physical security setting, it is most commonly associated with cyber security breaches. This is because many organizations have moved away from traditional methods of authenticating users, such as keys and ID cards, to digital systems that can be more easily bypassed.
One of the most common ways to carry out a tailgating attack is to simply follow someone through a door or access point that requires some form of authentication.
Threat Actor
A Threat Actor is an entity, whether it be a person, group of people or entity, that can threaten an organization’s cybersecurity.
A Threat Actor can be anyone from a disgruntled employee to an organized crime syndicate. They can use various methods to gain access to an organization’s systems, including spearphishing attacks, malware infections, and social engineering techniques.
Once inside an organization’s systems, a Threat Actor can steal sensitive data or sabotage critical systems. Organizations need to be aware of the threats posed by these actors and implement robust security measures to protect themselves against them.
Threat Hunting
Threat Hunting is the proactive search for malicious actors and activity inside an organization’s networks. Unlike other activities such as intrusion detection or vulnerability scanning, Threat Hunting is focused on identifying threats that may have already bypassed traditional security controls.
Threat Hunting is a critical part of any cybersecurity program, as it allows organizations to find and address threats before they can cause damage. Threat Hunters use various techniques to identify malicious activity, including network analysis, manual inspection of logs and data, and machine learning algorithms to identify anomalous behavior.
If you’re interested in learning more about Threat Hunting, several great resources are available online. The SANS Institute has a great introductory course on the subject.
Threat Intelligence
Threat intelligence is the process of monitoring, detecting, and analyzing cyber threats to reduce an organization’s vulnerability to them. Threat intelligence can be used to inform decisions about cybersecurity countermeasures, such as deploying new security technologies or changing user behavior. It can also help organizations identify previously unknown threats and understand how they might be exploited.
Threat Intelligence Platforms (TIP)
A threat intelligence platform (TIP) is a system designed to provide its users with actionable information about cyber threats. By gathering data from various sources and conducting analysis, a TIP can help an organization better understand its risks and take steps to reduce them.
When analyzing threats, TIPs typically consider the motivations behind an attack – such as political or economic gain – as well as its methodology and probable targets. This approach helps analysts not only understand what an adversary is trying to do but also anticipate their next move.
There are many different TIPs available on the market, each with its strengths and weaknesses. No single platform can offer everything, so it’s essential to choose one that meets your specific needs.
TrickBot Malware
TrickBot malware is malicious software used by cybercriminals to collect sensitive information from victims, including banking details and login credentials. Typically, TrickBot is distributed via phishing emails or drive-by downloads, and once installed on a victim’s computer; it can steal sensitive information and infect other computers on the network.
To protect yourself from TrickBot malware, be wary of email attachments and links from unknown sources, and keep your antivirus software up to date.
Trojan
A Trojan, in cybersecurity terminology, is a type of malware that disguises itself as something else to evade detection and infect a computer or network.
Trojans are one of the most common types of malware and can be used for various malicious purposes, such as stealing information or passwords, inserting ransomware into a system, or hijacking a computer’s resources to use for criminal activities.
U
User
A user is an entity that uses a computer system or network. In computing, a user is a person who uses a computer to perform tasks. In networking, a user is an entity that sends or receives data on a communications network.
V
Vulnerability Management
Vulnerability management is the processes and practices employed by an organization to identify, assess, and remediate vulnerabilities in its information systems. Vulnerability management aims to reduce the risk of exploitation of these vulnerabilities and the potential for damage to the Organization’s data or systems.
Vulnerability management programs generally fall into two categories: reactive and proactive. Reactive approaches wait for identified vulnerabilities to be exploited before taking action, while proactive strategies work to identify vulnerabilities before they can be exploited. Each has its benefits and drawbacks, but neither is inherently better than the other. Organizations must carefully weigh their specific needs and risks when deciding which approach to take.
Vulnerability Management Lifecycle
The vulnerability management lifecycle involves identifying, assessing, mitigating, and tracking vulnerabilities. It’s an integral part of any organization’s cybersecurity strategy, as it helps ensure that all vulnerabilities are identified and addressed promptly.
The vulnerability management lifecycle begins with identification. Vulnerabilities can be identified through various means, including internal and external scans from third-party vendors. Once a vulnerability is identified, it needs to be assessed to determine its severity. Mitigation measures can then be implemented to reduce the risk associated with the exposure. And finally, the vulnerability needs to be tracked so that its status can be monitored over time.
W
Web Application Firewall (WAF)
A Web Application Firewall (WAF) is a firewall specific to web applications. It sits in front of the web application and monitors all traffic between the user and the web application. If it detects any malicious traffic, it blocks it.
A WAF can be used to protect against various attacks, including Cross-Site Scripting (XSS), SQL injection, and cross-site request forgery (CSRF). It can also be used to protect against denial of service attacks and brute force attacks.
Whaling Attack
A whaling attack is a cybersecurity attack that targets explicitly high-level executives or other individuals with access to sensitive company data. The attacker sends a phishing email that looks very legitimate and tricks the recipient into opening an attachment or clicking on a link that installs malware on the victim’s computer.
A whaling attack aims to gain access to confidential information or financial records that can be used for fraudulent purposes. The attacker may also try to blackmail the victim into paying a ransom to keep the sensitive data secret.
X
XDR (extended detection and response)
Extended detection and response (XDR) is a security information and event management (SIEM) technology that provides a larger field of view across an organization’s network than traditional SIEMs. XDR retroactively collects data about incidents from multiple security products and services to give analysts more context about an event.
The goal of XDR is to provide a single platform for cybersecurity incident detection and response that integrates with an organization’s preexisting security infrastructure. By collecting data from multiple sources and correlating it using machine learning algorithms, XDR can give security analysts a more holistic view of the state of their network and better enable them to detect, investigate, and respond to incidents.
Y
Z
Zero Trust Security
Zero Trust Security is a term for cybersecurity models that don’t rely on predefined trust levels.
In a typical trust-based security model, users are divided into groups (such as “trusted users” and “untrusted users”) and access to resources is granted based on those groupings. The idea behind Zero Trust Security is that there is no such thing as a trusted user because any user could potentially be compromised.
Instead of using trust levels, Zero Trust Security models rely on rigorous authentication and authorization procedures to ensure that only authorized users have access to resources. This helps to prevent malicious actors from gaining access to sensitive data or systems.
Zero Trust Strategy
A Zero Trust Strategy is a security model where access to resources is granted on a “need-to-know” basis rather than a permissive “trust me” model.
This means that users are not automatically trusted just because they have been given access to a specific resource in the past. Instead, each user is assessed for trustworthiness on a case-by-case basis before being granted access to any resources.
This helps prevent malicious users from gaining access to sensitive resources by pretending to be someone else. It also helps prevent unauthorized access by users who may have malicious intent but do not currently have physical access to the network or systems they are trying to attack.
Zero-Day Attack
A zero-day attack is a security flaw unknown to the software or system developer. Attackers can exploit this vulnerability to gain access to systems or data.
Cybercriminals often use zero-day attacks to launch targeted attacks, as they can take advantage of the fact that the victim is unaware of the danger. In some cases, such attacks can be used for political or ideological reasons.

