Chris Lawrence is a journalist and chief editor at Wlan Labs. He has been writing about technology for more than ten years. He writes about everything ranging from privacy to open source software. His goal is to educate readers about important topics to help make their lives easier.
A User-Friendly Guide To Endpoint Protection
If you’re hunting for security solutions, you may have heard about endpoint protection. Unlike common phrases like antivirus or firewalls, this form of security is slightly less well-known but perhaps more important due to its effectiveness and comprehensive nature.
But what is endpoint security and why is it so important? We have everything you need to know here.
What Is Endpoint Security?
An endpoint protection platform (EPP) is one of the top security solutions that protect an organization’s devices and stored data. Endpoint protection works by examining files and potential threats. It can quickly detect malicious activity and increase the likelihood of data loss prevention.
What an Endpoint Protection Platform Protects Against
Cybersecurity threats are everywhere, and an organization’s endpoints are some of the most vulnerable.
There are various tools available to keep enterprise networks safe, but centrally managed security solutions like endpoint security focus on traditional attacks, including (and depending on the particular platform):
- File-based malware attacks
- Ransomware
- Fileless malware
- Polymorphic attacks
- Zero-day vulnerabilities
These threats typically come from outside organizations or occur during data leaks. As information is transferred, it’s particularly vulnerable to these types of attacks.
Rather than behavior-focused cybersecurity, this focuses on the threats themselves and identifying suspicious activity, and stopping hackers before they find success.

What Are Endpoints?
Extra security sounds great, but what exactly are the endpoints that these endpoint security systems protect? We’re all now working in virtual environments.
Even if you don’t spend all day at a computer, the chances are high that you depend on technology to interact with stakeholders and customers and store information. Your system that connects everything is your enterprise network.
You can imagine that as data transfers from one device to another or one software to another, these sources and destinations are endpoints.
Laptops, Tablets, and Mobile Devices
When considering cybersecurity, don’t think of your system as just one whole. Individual devices, like mobile devices and laptops, are each an essential component of your security, and each can be compromised.
Mobile endpoint devices and their security are more important than ever in today’s business landscape.
Offices are promoting BYOD (bring your own device) policies, allowing employees to bring a mobile device and use it as work equipment that accesses the organization’s network on premises.
These must be thoroughly protected.
Internet of Things (IoT) Devices
Many organizations depend on an internet of things to keep their devices connected over the internet. The more sensors, software, and equipment used to make up your internet of things, the more vulnerable you are to advanced, persistent threats.
You need anti-malware that will protect all. the tens, hundreds, or thousands of endpoints in your IoT.
Point of Sale Systems
Your point of sale system is what allows your customers to make purchases from your organization. Both them and your sales team need to know that the system is safe and protected.
Advanced threats can pose a serious danger to your customers and your system’s data. As sensitive customer information is transferred from the user to your system, your endpoint security must step in to keep it safe from point A to B.
The Importance of Endpoint Security
Are you still wondering why is this solution deployed? Here’s what you need to know:
Security for your enterprise networks is an integral component of protecting sensitive information. But your most sensitive data is most at risk when being transferred from one endpoint to another.
A data breach could cost your organizations both money and consumer trust.
Endpoint security uses continuous monitoring to stop hackers before they gain access. It has the remediation capabilities needed for protecting sensitive data before a data breach.
How Does Endpoint Protection Work?
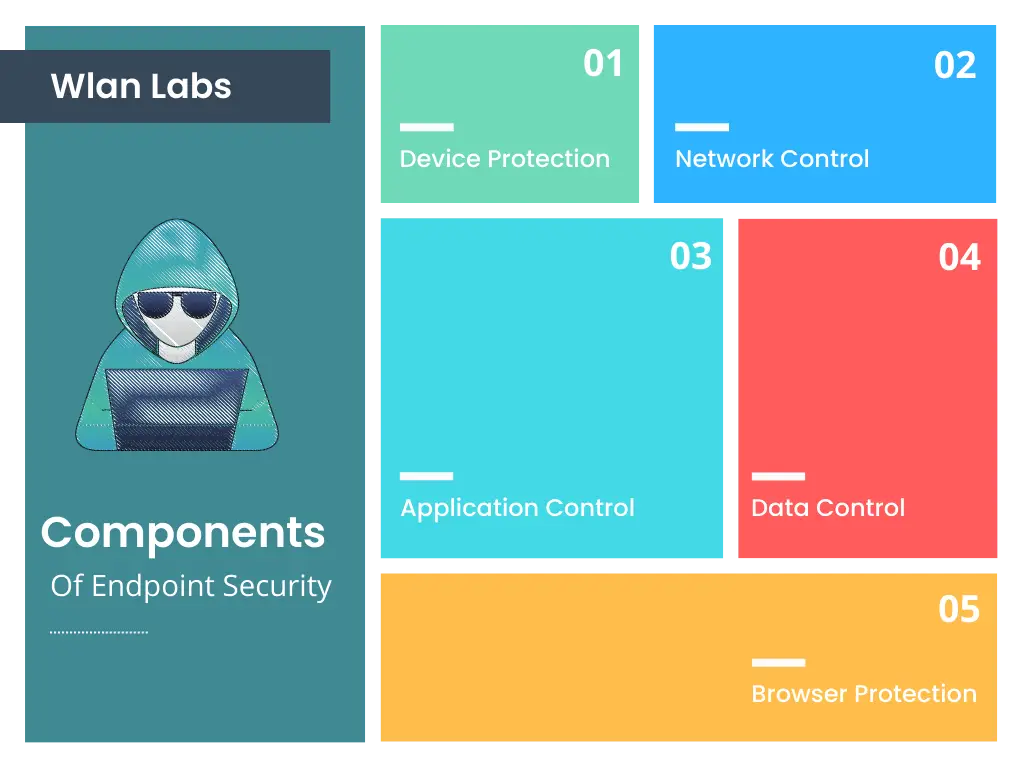
Endpoint security solutions refer to all the ways an organization works to protect endpoints. Good, comprehensive endpoint protection will approach this task from several angles, encompassing many security technologies, all in the name of endpoint security.
All of these come together to ensure a high speed detection rate, excellent response capabilities and work round the clock to keep your system safe. Learn more about the different ways this security system works.
Antivirus Software
Antivirus is an important part of an endpoints’ protection. But is endpoint protection the same as antivirus?
No. Traditional antivirus solutions alone rely on signature-based detection and focuses on only one endpoint. It only removes known viruses rather than engaging in proactive threat hunting.
Compare this to EPP which provides comprehensive endpoint protection for all connected endpoints in the enterprise network.
When it comes to the protection of sensitive data, antivirus software simply isn’t enough — you need endpoint security which includes antivirus systems in addition to other protection.
Endpoint Detection and Response
Perhaps the best part of any software you’ll find is the endpoint detection and response features. This features offers the investigation and remediation capabilities you need to stay ahead of hackers.
Malware can come at the most unexpected times from surprising sources. Your protection must always be ready.
Malware detection offers organizations an up-close look at exactly what files are entering, which set off the alarm bells, and how to act in defense.
URL Filtering
Can you think of how many websites you visit in a week? How many websites to click on for the first time? Any of these unknown sites for be attacks waiting to happen.
With endpoint security software, you don’t have to worry about clicking on a malicious site or downloading unwanted files.
This provides continuous detection to keep you only on trustworthy sites and protect you from suspicious downloads.
Application Control
Apps are part of our daily lives. We may download and use apps without hardly thinking about who’s on the other end of those nifty tools. But not all apps are as trustworthy as we want to believe.
With endpoint protection software, you get strict control of security settings to determine what apps can and can’t do on your network.
Even innocent apps can be used maliciously. This is where the importance of behavioral analysis of endpoint security comes in.
Just because it seems trustworthy initially doesn’t mean anything if its actions are suspicious.
Network Access Control
Network endpoints are a delicate part of your digital ecosystem. After all, a device connected to your network can do a lot of damage.
But with the right protection for your endpoints, including control over who can and can’t access your network, you limit the possibility of an attack.
Endpoint protection platforms investigate connection requests and give control over access. This firewall and data limitation protection will keep your network safe from threats by stopping access before it ever happens.
Browser Isolation
Don’t let a simple internet surfing session result in a ransomware attack that costs you thousands. Many threats lurk in your browser, and you may be utterly oblivious to the danger.
However, that doesn’t make the threats any less real.
Endpoint security software can provide you with browser isolation. Here, you can surf on a browser that isn’t connected to your sensitive digital assets.
If an attack does occur, it’s in this isolated environment with few consequences.
Cloud Perimeter Security
It seems every organization is going cloud-based. And why shouldn’t they? It’s an affordable way to store data, doesn’t require large, on-site equipment, and keeps data accessible to all team members across devices, increasing productivity.
However, cloud-based solutions may also leave your information vulnerable, just as local hosting also comes with risks.
Cloud providers aren’t responsible if your cybersecurity is lacking. Endpoint protection platforms form defenses around your cloud databases, keeping these endpoints secure.
Endpoint Encryption
Organizations aren’t always the most reliable for maintaining encryption measures across systems, but proper encryption is one of the best ways to stop a hacker in its tracks.
Data leaks may occur because of an attack or an unintentional slip. What’s essential is that protections are already in place to keep this event from being detrimental.
Endpoint protection platforms take care of endpoint encryptions for you. This means if data leaks during transfers, the leaked information will be encrypted, ultimately foiling the goal of attackers or prying eyes.
Secure Email Gateways
It seems in-person meetings are becoming a way of the past as the world goes virtual. This means that much of the information entering and exiting your organization is done over e-mails. And through this vulnerable transfer, hackers attack.
Endpoint protection sets up gateways for emails, continuously monitoring what goes in and out. If there’s any suspicious behavior, it can intervene and stop delivery as a means of remediation until someone else can step in and further investigate the attack.
Sandboxing
The best way to avoid future attacks is not to give potential threats access to your networks. This requires gathering threat information and determining if you can ultimately trust incoming files. This is where a sandbox as endpoint protection comes in.
A sandbox acts as a replica of your operating system. Here, threats play out, and you see what their intentions are without putting your system in jeopardy.
Finding Endpoint Protection Platforms
Examples of what were once considered sophisticated attacks are now child’s play. Hackers are only getting better at accessing our data, and endpoints must be thoroughly protected to avoid malware, ransomware, and data loss.
You need the best endpoint protection solutions, but how to pick one?
What Is Microsoft’s Endpoint Protection?
Microsoft is a top performer in many categories. But when it comes to the security solutions often included with Microsoft products, the endpoint protection solutions are lacking.
This is only the basics of what a typical user might need but won’t effectively protect your personal or sensitive information. You won’t get crucial protection features like device control or data loss protection.
While Microsoft endpoint security may be convenient, you’ll want to ultimately turn to third-party solutions to keep your enterprise networks safe.
What Is the Best Endpoint Protection?
With the importance of endpoint security software in mind, it’s not enough to go with the first option you see.
Hackers are constantly up-to-date on the latest ways to attack — you need a system that’s up-to-date on the latest protection methods.
Primarily, you need an endpoint security solution with fast remediation response times so you can handle dynamic security incidents effectively.
Consider cloud-based solutions as well — providing administrators visibility while constantly storing and analyzing past data.
Machine learning capabilities are also a plus. Machine learning keeps your system updated on attacks and identifies attacks in the future more accurately and quickly.
Start Protecting Your Corporate Network
From mobile devices to digital printers, you need to protect endpoints. Think of each endpoint as an open door to a hacker. Endpoint protection solutions close and lock the door.
If you or your team are handling sensitive data, this protection, along with other security technologies, is a must.
You can trust that your information is safe thanks to continuous monitoring and rectifying holes in your current protection system from the right endpoint security platform.
If you haven’t started shopping for endpoint security, it’s better late than never. Use this guide to better understand how to find the right solutions, and you’re on your way to finding the best providers for your business.
Endpoint Security Reference Links:
- https://venturebeat.com/2022/03/03/ai-brings-greater-resilience-to-self-healing-endpoints/
- https://www.researchgate.net/figure/Comparison-between-file-based-malware-and-fileless-malware_tbl1_338576309
- https://www.forbes.com/sites/lilachbullock/2019/01/21/the-future-of-byod-statistics-predictions-and-best-practices-to-prep-for-the-future/?sh=532c149b1f30