
Chris Lawrence is a journalist and chief editor at Wlan Labs. He has been writing about technology for more than ten years. He writes about everything ranging from privacy to open source software. His goal is to educate readers about important topics to help make their lives easier.
Are you interested in learning about MFA solutions? In this article, we will go over the best multi factor authentication apps out there.
But, before you check out the list, below is a short explanation of what exactly an MFA or Multi-factor authentication solution is.
What Exactly is a Multi-Factor Authentication Solution?
Also known as MFA, multi-factor authentication is a method that will require the user to give them two or more verification factors to have access to an application, online account, VPN or something else you need access to for work but has sensitive information that cannot be shared to the public.
Multi-factor authentication is central to a strong identity and access management or IAM policy. Most security systems will simply ask you for a username and password, while an MFA may ask you for more than one way to verify your identity.
The whole point of an MFA multi factor authentication app is to deter hackers and decrease the possibility of a cyberattack happening and being successful.
How Does Multi-Factor Authentication Work?
MFA will work by making it so that users must input additional verification information or factors that identify them as who they say they are.
For example, One of the most common systems will send users a one-time password or OTP that is sent to an email address or SMS so that the person can input that code and prove that they are who they say they are.
Are there Different Types of MFA Authentication?
There are three main types of MFA. The first one is essentially a password or pin, which will be something that you know. Think of this one as knowledge.
The second type will be based on something that you have, such as a smartphone or badge. Think of it as possessing a key to get into a system. Finally, you can input biometrics like voice recognition or a fingerprint. Think of this one as something that you are.
There are, of course, many different types of MFA, but these are by far the most common and safest ones out there.
With that in mind, it is finally time to move on to taking a look at eleven of the best MFAs out there.
Top 11 Best Multi-Factor Authentication Apps
Consistent and fully verified encryption and multi-factor authentication guarantees your company data is protected in compliance with laws and regulatory rules.
Prevent data breaches with quick & seamless deployment. A powerful encryption engine managed natively by the ESET remote management console.
ESET Secure Authentication
This MFA is a market-leading vendor that specializes in lightweight and user-friendly cybersecurity solutions.
They are a secure authentication enterprise designed to lower the risks of passwords being stolen when those using it are asked to verify their identity in one or more ways before they can get onto the system and have access to everything they need.
At the moment, ESET supports more than a hundred million uses across the whole world. The key to this success is the wide range of authentication method solutions they offer.
For example, they support on-site apps and web and cloud services like Office 365 and Dropbox via SAML protocol integration.
This makes it so that ESET can be used by many users no matter what device they use. This method also ensures compliance and data security across every single one of a business’s systems.
This MFA two-factor authentication app would be a good fit for large enterprises or small businesses. For this reason, it is quite easy to manage, and there is no need for an IT resource team to get it up and running and maintain it.
ESET would be suited for those of you looking for an intuitive and powerful solution for an organization. If you want an authentication system with two factors across your business system, this is ideal as it will work regardless of where the company is hosted.
Prove MFA

Prove has an Auth solution, a super-comprehensive mobile-first suit with a wide variety of authentication protocols ranging from OTP to more sophisticated mobile authentication, including biometric authentication.
This authentication suite can be used by clients and be tailored to have high-risk or low-risk transactions to make it less likely that friction occurs when prioritizing the customer’s experience.
Prove also has phone-centric identity™ technology, which leverages the mobile phone and phone number as the main authenticator.
By doing this, clients can deterministically authenticate customer identities with almost complete certainty. Prove uses this ‘Yes or No’ process instead of a probabilistic approach.
There are many companies that use Prove inclusion, over five hundred banks, eight of which are the best in the United States.
These banks use Prove to make fraud mitigated, increasing revenue and, by extension, lowering operating costs. This whole process makes the customer’s experience better across every channel.
Prove is a great MFA if you are looking for something with a strong security identity far better than many traditional multifactor authentication methods with risk-based authentication.
On top of having an app that verifies whether a phone number belongs to a user, Prove’s Trust Score ™ has a real tile risk scoring feature that allows you to look at reputation indicators from real-time signals.
This could be looking at something as simple as how long a number has been used and where the phone number has been used.
This is done by using a real-time dynamic and behavioral context risk scoring system which helps to build a holistic identity score that is much better than improving account scrutiny without increasing the complexity of your security team.

Cisco Duo Multi-Factor Authentication

Cisco gained Duo Security in 2018, they provide an access management solution that ensures employees have secure access to corporate accounts. This helps businesses reduce credential-based security risks while also meeting regulatory compliance.
Duo has a two-factor authentication app solution that will support many different authentication methods. This will make it much easier for any users to log onto their accounts securely regardless of what kind of device they are using or the location they are working.
You can get Duo’s zero-trust solution in five plans. So, you will be able to get a more compact solution that will better suit small teams, or you can get a comprehensive version that will be better suited for large or corporate businesses.
The choice is up to you. This plan makes it so that Duo can help companies of varying sizes find a way to secure and monitor their access accounts.
The Duo mobile app is what you will use for Duo Security’s Zero-Trust MFA, this app will allow those using it to verify their identities through the app itself. This process makes it so that each user can easily be approved or denied when attempting to log in.
Duo is great because it is also integrated with universal second factor authentication tokens, hardware tokens, mobile passcodes, U2F USB devices, and biometric controls built into the server device, like Face ID, for example.
This is a great feature for companies that are looking to use an MFA that will be able to enforce a wide variety of authentication controls across various devices when their session begins. This will ensure that there will be minimal disruption when various people are logging on.
The admins can use the management console to configure adaptive authentication policies based on user location, device and role factors.
Duo will check the login data with the policies for anomalous access attempts, and this will ensure that further steps will be taken to verify any login attempts.
The program is smart as it will only ask for further verification when it is required based on the login attempts and the policies it is checking the data against. This makes the whole process safer and more efficient overall.
Typing DNA Verify 2FA

This MFA will give you a passive authentication technology that gives unparalleled protection against someone compromising your account. This process should not mean that the users experience any undue friction, nor will they need to apply any undue effort to this process.
Typing DNA replaces SMS OTP codes that rely on simple typing of four words, not dissimilar to CAPTCHA, which is then verified while you are inputting biometric information to authenticate your access to the account.
Typing DNA skips this laborious process without impeding the security of the account. Isn’t that fantastic!
Many experts have found Typing DNA impressive due to the user-friendly interface and the seamless login experience they saw when they tried this MFA.
Typing DNA always lets you pick between two plans. The first one is called the starter plan, which will allow you to authenticate about one thousand users for free for a limited time.
The paid plan can accommodate as many authentications as you like and, at the time of writing, only cost one cent for every active month that it was in use.
This MFA is suited to organizations of various sizes. You just need to be sure that you are happy with an MFA that uses methods that are not traditional to authenticate users. But, this is quite a cheap MFA that is well known for its security.
JumpCloud Project

This MFA is essentially a cloud directory platform programmed to enable a company to manage and keep tabs on the identity of those attempting to access the tools.
There are several management tools that are used to help with this. For example, multi-factor authentication, single sign-on, mobile device management, and patch management.
These multi-factor authentication apps solutions can be accessed through a single central interface.
This MFA is particularly good for those who need something super easy for admin and IT to use and secure accounts and devices. JumpCloud implements and maintains a zero-trust policy as well as demonstrates compliance while maintaining data protection standards.
This MFA has been used by over a hundred and fifty thousand organizations worldwide and has consistently maintained its reputation as one of the best MFAs out there.
Most users have found this multi-factor authentication solution user-friendly and easy to manage and implement across an organization.
JumpCloud is best suited to medium to small companies on the hunt for an MFA that is easy to manage and super secure with minimal effort by both admin and users.
Twilio Authy

Twilio has a 2FA app for your smartphone that consumers or developers can use. Whenever a user logs onto an account, or a transaction is made, Twilio will make a token code that is entirely unique.
This MFA then authenticates the user and their identities on a mobile app which then helps to make it less likely that the account will be compromised or stolen from.
This WFA is extremely popular with small businesses, which is why there is so much positive feedback that compliments Twilio on how fast it is and how it can prevent information breaches.
Twilio is best suited to those on the hunt for 2FA for all their accounts. This MFA will shine if you have a smaller team that requires all the users to authenticate their identities.
OKTA Adaptive Multi-Factor Authentication

This MFA will secure access to all aspects of your business accounts by way of authentication for every single one of your partners, customers and employees.
This service has been created to be an easy to use, secure and smart service. OKTA has focused on making its admin portal super easy to use and easily enforces MFA across the whole organization. The implemented policies will enforce contextual-based login in times of hardship.
This means that users will be prompted to verify their accounts using contextual factors. This is so that the users’ productivity will only be affected when it is absolutely necessary.
Many customers found that OKTA was full of fantastic features that made it intuitive and effective. Many people who used this MFA were delighted to find that it was easy to sign into quickly and that several options were available for verification purposes.
This means they could access the account with or without their phone. This MFA is recommended for the middle of the range to large enterprises looking for an MFA with various authentication policies and options while still keeping everything user-friendly.
HID Identity and Access Management

This MFA is one of the leading cybersecurity vendors which offers a wide range of enterprise-grade features.
Best of all, this MFA is user-friendly and has easy-to-use identity verification that anyone should be able to use easily.
HID has an advanced multi-factor authentication solution that is a huge part of their access management suite, this solution runs alongside identity and risk-based products that the admin can manage.
These Identity and access management suites, also known as IAM, can make it so that IT teams can manage and secure employee access to physical assets and logical assets.
HID is a vast number of user identities that exceed over eighty-five billion worldwide. The fact that they offer advanced MFA makes it so corporations can have safe access to networks, VPNs, and various cloud apps like Office 365.
On top of having a central management console feature and robust reporting capabilities, HID also gives you the option to allow administrators to find out how many people are using the accounts and who can access them from what part of the network.
This type of advanced MFA can be deployed on-prem or into the cloud, which is why it is so easy to set up and flexible.
As a result, the advanced MFA that HID provides is a great product for companies or organizations with plants to grow.
It is also ideal for people that have their employees working from home and in the office or companies that have more than one office location.
This MFA is recommended to people needing a solution for their mid-sized organization or enterprises searching for a program to secure and verify people’s access to corporate assets on many different business levels.
Manage Engine ADSelfService Plus

This MFA is properly established as a software vendor that forms the IT management division of Zoho Corporation, a business software company.
Manage Engine is a very powerful MFA which uses several authentication methods such as password management, multi-factor authentication and single sign-on solutions.
These are used to aid organizations with gaining better secure access to various machines like Windows, macOS, VPNs, Apps, endpoints, Outlook Web Access, and LinuxOS.
This MFA comes in three pricing tiers called Free, Standard and Professional.
The main thing you need to be aware of with these plans is that Endpoint MFA will only be available for those of you that have chosen the professional tier, which can cost quite a lot of money every year.
The average price has been about $1200, giving you about five hundred domains every year.
When it comes to the installation of Manage Engine, it can be installed on machines, devices or servers, depending on what you need.
The admins can pick if they want to install a thirty-two bit or a sixty-four-bit version, but this will depend entirely upon their requirements for this MFA.
Many people using Manage Engine now have found it simple to set up, easy to deploy, and an easy-to-use platform.
The main issue they experienced was that it was slightly outdated, which may not suit everyone’s needs. This MFA is recommended to those of you that have larger organizations that are in Healthcare, government, IT or Finance.
Thales SafeNet Trusted Access

This MFA provides safety for data on the cloud. On top of that, they have a wide range of solutions that will work for various user cases. This includes human and machine identity verification, access authentication, data discovery and encryption. Thales is a well-known and trusted MFA.
The solution they have makes it so that organizations can manage the access their users have to apps and cloud services owned by the company.
All of this happens through a singular unified platform, making it much easier to use and set up. Thales has a Trusted Access Feature with multi-factor authentication and contextual authentication, both of which work to assure the safety and security of the company assets.
Thales Trusted Access MFA is quick to deploy onto the cloud and will be flexible and easy to scale as the corporation grows larger.
This platform will support authentication across many platforms, including iOS, Mac OS, Windows, VPN, Cloud Services, and Android Operating Systems.
Many users have found that Thales is super easy to use and that the customer support is strong with this particular MFA. This MFA is best suited to people needing an integrated SSO with fairly powerful authentication capabilities.
Ping Identity Multi-Factor Authentication

This MFA is an identity management suite with various features that will help with the identification management of its users. Single, Sign-On, Multi-Factor Authentication and Directory are included with Ping.
The MFA itself is usually distributed through the cloud, which gives you an identity-as-a-service model included with this is a software-based solution.
Ping is focused on allowing you to easily integrate with customers that own an enterprise. This means there is more allowance for admins to use SDKs, APIs and Integration Kits to streamline the implementation with existing infrastructure.
Many customers have been super pleased by how easy this MFA is to build, secure and maintain. There have also been reviews that focus on how reliable Ping is and how flexible its authentication platform is, as it can easily meet the company’s needs.
With Ping, it is easy to log on and access all the needed apps. This MFA is best suited to large organizations and companies as it is quite easy to integrate across various platforms, and it is flexible in how it is deployed. On top of that, it can adapt to authentication policies.
Best Multi Factor Authentication Apps FAQ
You most certainly have a few questions about MFAs. In this section, several questions will be answered on this topic to help you better understand it.
Why is MFA Essential?
The main job of an MFA is to improve the security of an organization, small business, enterprise or company by making it mandatory that those accessing the information must submit certain information that identifies them as who they say they are.
This will be on top of a username and password as they are more vulnerable to cyberattacks. By extension, a username and password can make it easier for cyber criminals to steal intimation.
What is the Different Between 2FA and MFA?
Two-Factor authentication, or 2FA, will make users submit two types of authentication. At the same time, MF will require AT LEAST two forms of verification, but they can ask for more types of authentication. So, 2FA is an MFA, but Not all MFAs are 2FA.
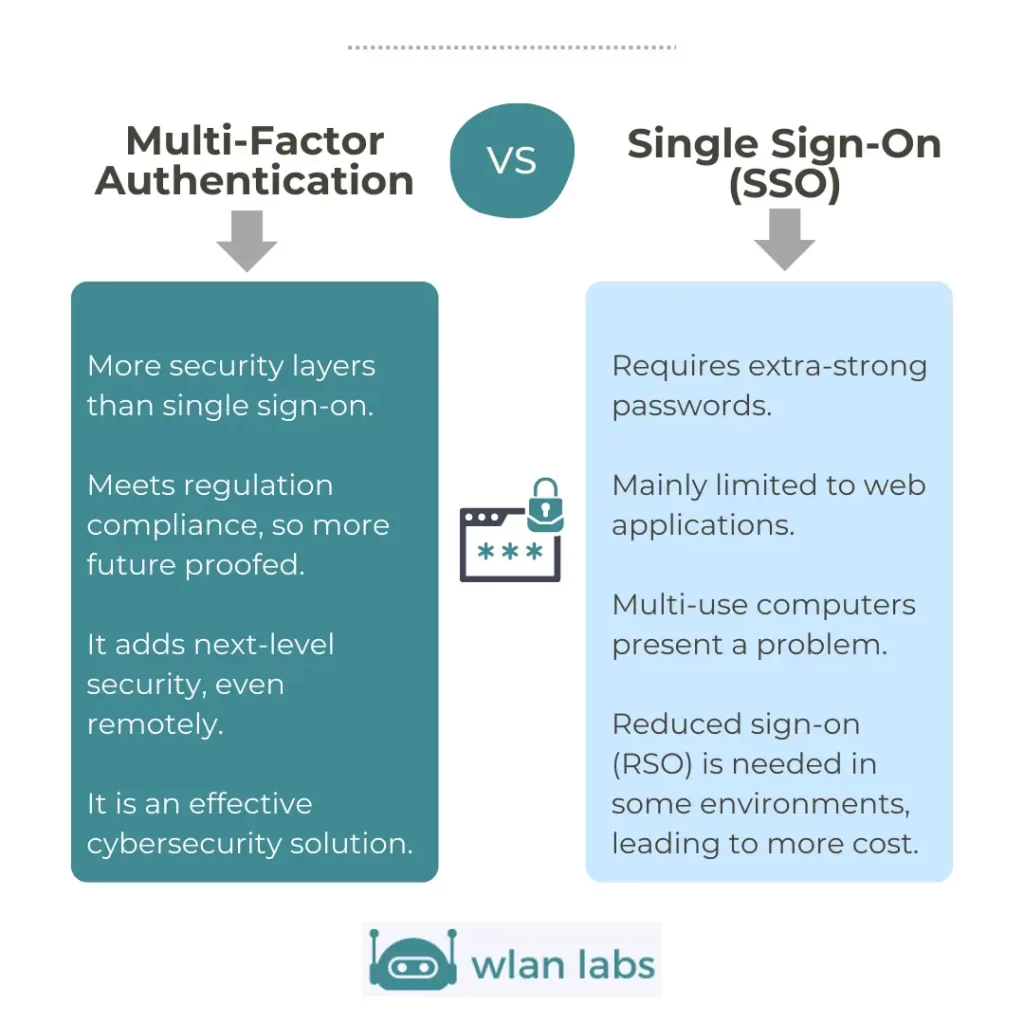
Which is Better: SSO or MFA?
SSO is better suited to users, but there are more security risks associated with it, while MFA is more secure, but it will be less convenient for users.
So, you will need to decide what is more important to you when choosing between SSO and MFA.
Is SAML the Same as MFA?
SAML is most often used for authentication and will enable SSO. But it can also be used to configure MFA between different devices.
If you apply this to an enterprise where various hosts use different SPs, SAML can enforce MFA in several ways. This means these two are not the same because they work together to the same end.
Does Google Authenticator Work?
This authenticator app is based on the time-based one-time password or TOTP system.
This system generates a six-digit passcode that factors in the current time so that each passcode will be unique. These passcodes will change every thirty to sixty seconds so that it is secure.
So, yes, Google authenticator does work, but there are likely to be better MFAs out there that will work better.
Final Thoughts
MFA is super important and something you will need for enterprises or organizations. It will enhance security by making it mandatory that people using the system identify themselves with more than a simple username or password.
That is not to say that usernames and passwords are useless but using them alone will make the enterprise more vulnerable to cyberattacks which means that information can be stolen.
By making it so that an MFA must be used and users must provide verification such as a thumbprint or a hardware key, you can have confidence that your enterprise or organization will be safe from cyberattacks.
We hope you have found our best two-factor authentication app guide helpful and welcome any comments you might have on the subject.


