
Chris Lawrence is a journalist and chief editor at Wlan Labs. He has been writing about technology for more than ten years. He writes about everything ranging from privacy to open source software. His goal is to educate readers about important topics to help make their lives easier.
So what is email encryption and why should you care? By the end of 2023, there will be 4.3 billion active email users in the world according to Radicati.
Of course, many people have more than one email address, but around 50% of the world’s population has an email address that they use. That is hardly surprising, especially considering how many things require an email nowadays.
While many people use personal email addresses for things such as ordering online, contact details, and so on, most workplaces also use email addresses.
Within business, millions of emails are sent every single day regarding things such as meetings, invoices, and communications with customers and suppliers.
Is Email Secure?
When you consider all the sensitive things that email is used for, it will come as a real surprise when you discover that it isn’t secure.
First, it is important to understand how email works. Email is essentially a way of sending messages electronically.
When you send an email, the message is converted into code and then sent to the recipient through the miracle that is the internet. The recipient’s computer then decodes the message and displays it.
You should always be careful about what information you include in an email, as it could potentially be read by anyone who has access to the server it is stored on.
Email accounts can easily be compromised by hackers, and attackers, through the use of phishing emails.
All it takes is one click on a very convincing phishing email, and all of your email communications can be accessed by cybercriminals. Not only will they get access to the emails themselves, but to all the attachments (including images and documents).
If you want to make your emails more secure, then you should use an email encryption service. This service will encrypt your information as it travels between your email address and the recipients.
This means that even if it is hacked, the hacker will not be able to access the information within the email. But this is just scraping the surface of what email encryption is.
In this guide, we’ll be taking a look at what email encryption is, how it works, and how it can protect your organization. So keep on reading to find out more.

What is Email Encryption?
First things first, let’s take a look at what email encryption is. As we have already touched upon, email encryption effectively adds more security to your emails.
There are two different styles of email encryption that exist, they are:
- End to End email encryption.
- Encrypting an email in transit (TLS).
TLS encryption is fairly standard, and most email providers use it. This includes Microsoft and Google.
Essentially TLS encryption ensures that an email cannot be read while in transit. So, from the moment it is sent from the sender till the recipient receives it, it cannot be read by anybody else.
There was a time when TLS encryption didn’t exist, and back then, it was fairly common for cybercriminals to read emails while they were in transit.
As a lot of business emails contain sensitive information, this man in the middle hacking meant that hackers were able to find out a lot about businesses that they shouldn’t have known. As you can imagine, this would be incredibly damaging for businesses.
But for many years, TLS encryption has been standard for most email suppliers, and many would consider this to be secure.
While TLS encryption offers more security than no encryption, it still only protects emails while they are in transit. It doesn’t protect emails sitting in the recipient’s inbox, meaning that skilled cyber hackers could still gain access to a business’s private emails.
That is where end-to-end encryption comes in. End-to-end encryption ensures that an email will only be received by its designated recipient. The email providers themselves cannot even read these emails.
When end-to-end encryption is used, the emails are encrypted by the sender. They can then only be decrypted by the intended recipient.
This is done using public keys shared between the sender and the receiver. It is very complicated, which is why end-to-end encryption makes it virtually impossible for hackers to access your emails, private messages, and attachments.
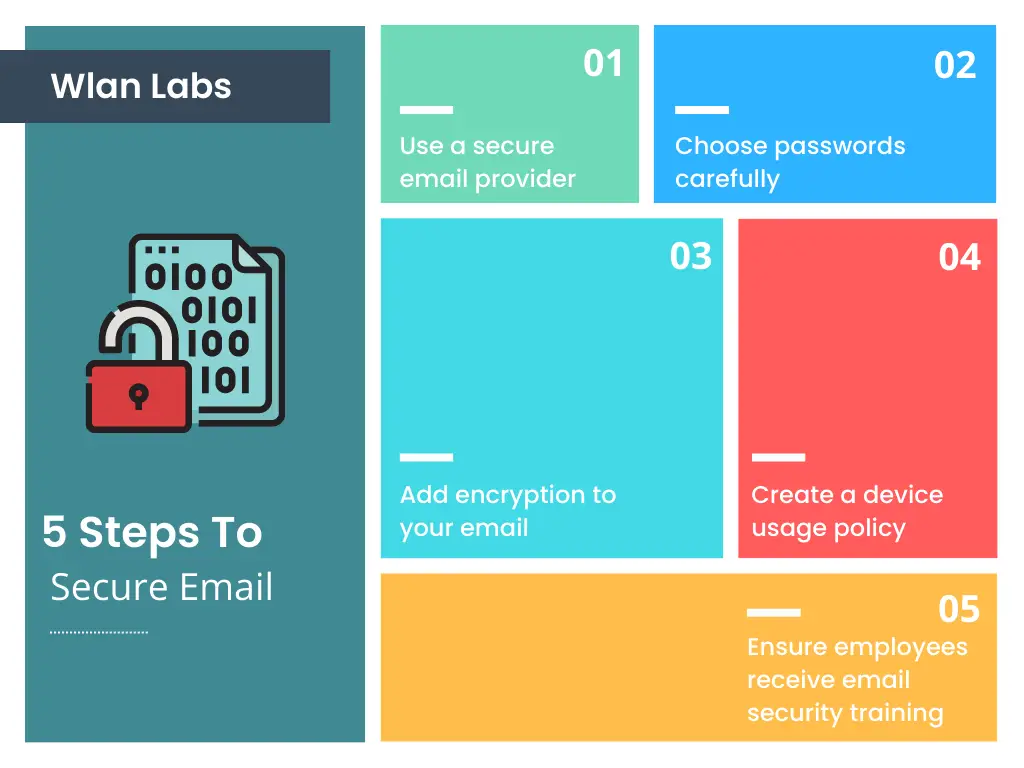
How Do I Read An Encrypted Email?
To read an encrypted email, you must have the proper encryption key. The email sender usually provides this key, which is used to decode the message.
Once you have the key, you can use various methods to read the encrypted message. One popular method is to use an online tool such as GPG4usb.
This tool allows you to decrypt the message using your web browser. Another option is to download and install a stand-alone program such as PGPy.
This program can be used to decrypt messages offline. No matter your method, ensure that you keep your encryption key safe and secure.
Otherwise, anyone who has access to it can read your encrypted emails.
What Does It Mean When An Email Is Not Encrypted?
When an email is not encrypted, it means it is sent in plain text. This means that the email can be read by anyone who can access it.
In addition, plain text emails are susceptible to intercepting and being read by third parties. To avoid this, it is important to encrypt your emails.
Email encryption scrambles the contents of an email so that only the intended recipient can read it. This way, even if your email is intercepted, the person would not be able to read it.
As previously mentioned, there are a few different types of email encryption, but the most common is SSL/TLS encryption. Most major email providers use this type of encryption, and it is generally considered to be very secure.
However, it is important to note that email encryption is not foolproof. If an attacker has access to your account or the recipient’s account, they may still be able to read your email.
For this reason, it is important to use a strong password and to only share your account with people you trust.
The Best Solution: Enterprise Email Encryption
End-to-end email encryption can be very confusing. That is why lots of businesses struggle to know how to implement this within their companies.
The solution to confusing end-to-end encryption is simple: using an enterprise email encryption service. These solutions will provide your organization with end-to-end encryption, allowing users within the organization to effortlessly encrypt their emails.
Enterprise email encryption does all the hard work, so you won’t have to. It takes a lot of effort for an admin to encrypt emails manually for an organization. In contrast, an enterprise email encryption service will allow employees to simply encrypt their emails with the click of a button.
It might be possible for sensitive emails to be automatically encrypted without employees having to do a thing.
There are a couple of different enterprise email encryption services to choose from, and the majority of them are cloud-based. Usually, they require a plug-in installed on your email provider, and then they are good to go.
Many enterprise email encryption services also provide a management dashboard, allowing admins to monitor where encrypted emails go.
This dashboard also provides more control, allowing the admin to revoke the ability to print emails, stop email forwarding, and lots more.
All in all, an enterprise email encryption service will not only provide extra security against hackers but from internal problems in a company too.
Things to Look For
Now that we’ve told you all about how beneficial an email encryption service can be for you and your company, you probably want to know what you should look for.
There are two main things that you should be looking for they are…
Security
Of course, the most important thing you should look for in an email encryption service is a high level of security.
The main reason you would use an email encryption service is to protect your emails from hackers, so a good level of email security is vital. It is best to look for a company that offers high security while also being compliant with data protection regulations.
Ease of Use
Email encryption can be complicated, which is why you would use a service provider for this. With that in mind, it is best to look for a service provider that is easy to use. Otherwise, it defeats the purpose of using an email encryption service in the first place.
The Pros and Cons of Different Email Encryption Methods
Encrypted PDF
This encrypts the content that is attached to the emails by encrypting the Office, ZIP files, and PDFs you might attach.
Pros
- Allows senders and recipients to access encrypted content straight from their inbox.
- Secures passwords that are sent via PDF.
- Ensures all documents are delivered whole and intact.
Cons
- No control over the attachments being forwarded.
TLS Encryption
Encrypts the contents of an email while it is in transit from sender to recipient.
Pros
- Easy to use.
- Easy to deploy.
- No extra steps are needed when sending emails.
Cons
- Only protects the contents of an email while the email is in transit.
Is Gmail Email Encrypted?
The answer is a bit complicated. Gmail uses a technology called SSL/TLS to encrypt all communication between your browser and Google’s servers.
This ensures that anyone who tries to intercept your traffic will only see gibberish. However, once your email reaches Google’s servers, it is no longer encrypted.
This means that Google employees can read your emails if they want to. In addition, government agencies can also request access to your emails through the legal process.
However, it should be noted that Gmail does employ automated systems to scan emails for certain keywords.
These keywords are used to target ads, and the data is not shared with any other Google products. As a result, your privacy is still protected to some extent.
How Do Hackers Use Encryption?
Encryption is the process of transforming readable data into an unreadable format. This is done using an algorithm and a key.
The key is known only to the sender and receiver of the data. The algorithm is designed to be reversed using the same key.
Hackers use encryption for two main reasons:
- First, it can help them to avoid detection by security systems. If data is encrypted, it can appear random and meaningless to anyone who does not have the key. This makes it much harder for security systems to identify hacking activity.
- Second, encryption can help hackers to protect their data from being accessed by others. If a hacker’s data is encrypted, even if it is stolen, it will be difficult for anyone to read it without the key.
There are several different types of encryption that hackers may use. One common type is symmetric-key encryption, which uses the same key for encrypting and decrypting data.
Another type is asymmetric-key encryption, which uses two different keys, one for encrypting and one for decrypting.
Hackers may also use steganography, a type of encryption that hides data within other non-secret text or data.
Summary
In short, emails are commonly used within businesses to communicate internally among staff and externally with suppliers and customers. However, emails aren’t that secure.
This guide has covered what email encryption is and why you should use it to protect your organization. Thanks for reading!

