
Chris Lawrence is a journalist and chief editor at Wlan Labs. He has been writing about technology for more than ten years. He writes about everything ranging from privacy to open source software. His goal is to educate readers about important topics to help make their lives easier.
The Wlan Labs team are frequently asked: how to stop phishing emails and how to prevent phishing attacks overall. How often have you received emails from someone claiming to be from your bank or credit card company asking you to verify your account details? These scams are called phishing attacks, and they happen every day.
Phishing attacks are a type of social engineering where criminals send malicious emails pretending to be legitimate institutions such as banks, credit card companies, etc. The goal is to trick you into giving away sensitive information.
Phishing attacks are becoming more sophisticated and harder to detect. They usually involve fake websites designed to look like real ones. If you receive suspicious messages, don’t respond immediately. Instead, call your financial institution directly.
If you think you may have been the victim of a phishing attack, contact your financial institution immediately.
What Exactly Is A Phishing Attack?
Before discussing how to prevent phishing attacks, we must understand more about it. Phishing is a broad term that includes many techniques. It is a type of social engineering attack designed to fool users into giving away sensitive information like usernames and passwords.
While there are many ways to get employees to give out personal information, phishing is often the easiest.
Hackers send emails or text messages that appear to come from legitimate companies. These emails usually contain links leading to websites that mimic real businesses.
Users are tricked into believing they are logging onto a legitimate website when they are accessing a fake site that collects user credentials.
Once the hacker has access to an employee’s account, he or she will likely move on to other accounts.
How To Stop Phishing Emails And Build Protection For Phishing Attacks?
How can you protect yourself against cyberattacks and stop phishing emails? One of the best ways to prevent phishing scams is to install anti-phishing software.
Anti-phishing software will help you identify suspicious emails and websites before you click through them. You should also avoid clicking links in emails unless you’re 100% sure that they’re legitimate.
If you get an email asking you to update your password or log into your account, you should always check the website URL in the email. If it doesn’t match what you expect, you should assume that the email is fake and delete it immediately.
Barracuda’s research shows that email phishing attacks are rising at an alarming rate. These attacks are designed to steal personal information, including passwords and credit card numbers, and are often delivered via social media platforms like Facebook and Twitter.
Phishing emails are often sent out through legitimate channels, making them hard to spot until after they’re opened.
To prevent this attack vector and how to prevent phishing attacks, you can use several tools to help protect your users and data.
The following are the top ways for organizations and individuals to protect themselves from phishing attacks:
- Use strong passwords.
- Enable two-factor authentication.
- Avoid clicking links in emails.
- Don’t download attachments from unknown senders.
- Scan your inbox regularly for suspicious messages.
- Check out the sender’s domain name.
- Never give personal information to someone you don’t know.
- Always verify phone numbers before giving out any sensitive information.
- Be wary of social media scams.
- Keep an eye out for signs of identity theft.

Those Pesky Phishing Emails: How To Prevent Phishing Attacks
Phishing attacks are often very effective because they mimic legitimate communications. These fake messages usually contain either links or attachments.
When someone clicks on the link or opens the attachment, they may download malicious software onto their device. Phishing scams are also very common. Users should never give out personal information to people they haven’t met in person.
If you receive an email that looks suspicious, contact the sender immediately. Never click on any links or attachments.
Phishing is when someone emails you or texts messages pretending to be another company or individual. If your bank emails you saying your account has been frozen, it’s probably not real.
But if you get an email from a friend telling you that your account has been compromised, it might be a phish. A phishing attack can also happen through other channels, including social media sites, websites, apps, and even voice messaging services.
Business Email Compromises And Spear Phishing
When considering how to prevent phishing attacks, you need to factor in the threat of spear phishing. Spear-phishing is when hackers impersonate a trusted source, like a business contact, and ask you to give out your personal information.
They may even ask you to make a payment. These attacks are highly effective because you usually won’t think of a trusted contact or a business you’ve worked for before as an attacker.
A spear-phishing attack attempts to trick someone into revealing information through deception and manipulation. Spear-phishing attacks often steal sensitive information like credit card details, login credentials, and passwords.
These attacks also spread malicious software, such as viruses, Trojans, adware, and ransomware.
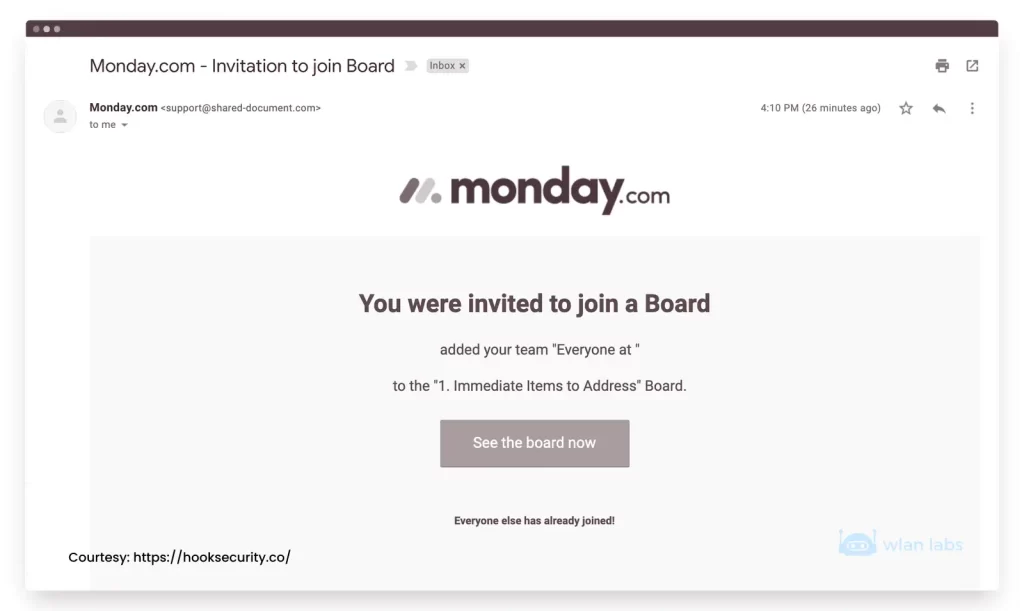
Phishing Example Email 1 (monday.com)
Main Phishing Style Websites
Phishing is a type of social engineering attack that involves fraudulent electronic messages that appear to be sent by someone else, usually an individual or company with whom you have an existing relationship.
These messages often contain malicious links or attachments that exploit vulnerabilities in web browsers or mail clients to install malware on your device.
Phishers aim to trick recipients into divulging personal information like usernames, passwords, credit card details, or other sensitive information.
Cybercriminals behind these attacks spend millions of dollars each year creating new techniques to steal money or valuable information from unsuspecting victims.
A similar incident happened last year when a hacker group inserted 22 lines of code onto a website belonging to British Airways, directing a few of its users to a fake website asking them to log in and enter credit card details.
The hackers could obtain personal information on 500,000 customers, and British Airways were later fined £183 million for not protecting customer data under GDPR.
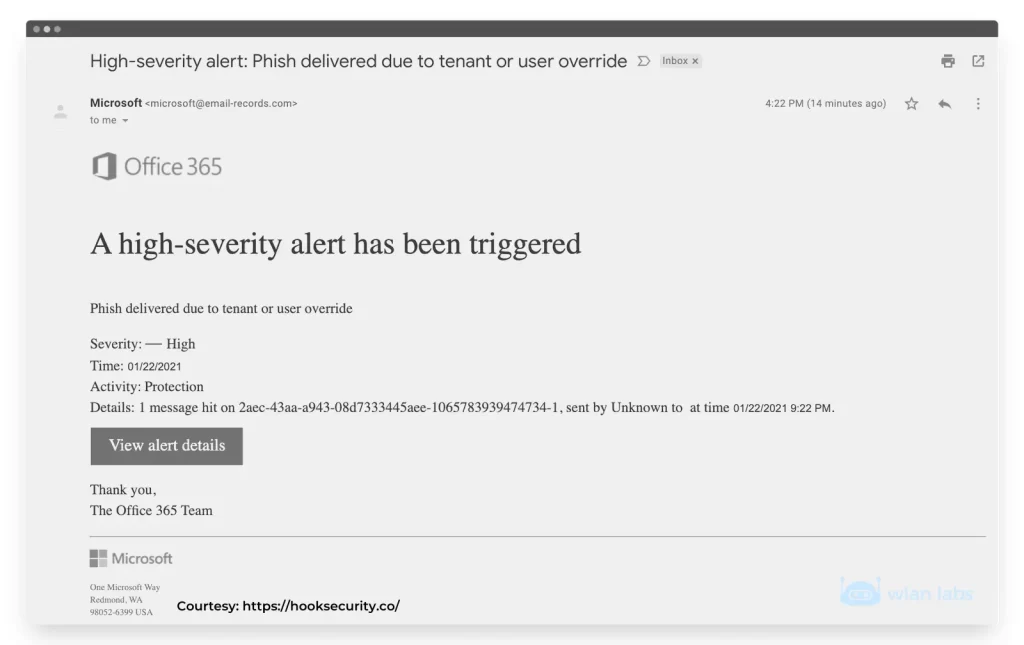
Phishing Example Email 2 (office 365)
Why Exactly Can Phishing Be So Damaging?
From the example of British Airways alone, you can see how damaging phishing attacks are.
Phishing accounts for about 90% of all data breach cases, and the average cost per breach is around $3.8 million dollars. 76% percent of companies report being a victim of phishing attacks last year, and that number is likely to increase this year.
The main cause of phishing attacks being so effective is that they slip through gaps in email and web technology.
Email clients like Microsoft Exchange, Office 365, or Google Suite will often block messages containing malicious links or ones that seem suspicious. However, attackers can easily bypass these filters by sending emails using spoofed identities.
As a result, businesses commonly use email clients like these for their internal communication. These platforms will filter some malicious emails, like those that contain overtly malicious links or appear suspicious.
However, these filters won’t catch everything, and attackers can easily bypass them by sending emails using spoofing identities.
Phishing isn’t just about sending out fake emails. Phishers can also use social engineering tricks to get you to click on a link, enter your password, or other sensitive information. These scams are often disguised as legitimate sites, like banks or online retailers.
For example, when you log onto your bank account, there’s usually an option to “forgot password”. If you follow the instructions, you might end up at a website that looks exactly like your bank’s login page.
But instead of displaying your username and password, it asks you to confirm your details using your phone number, birthday, or your mother’s maiden name. Once you’ve entered them, the scammer can access all your money.
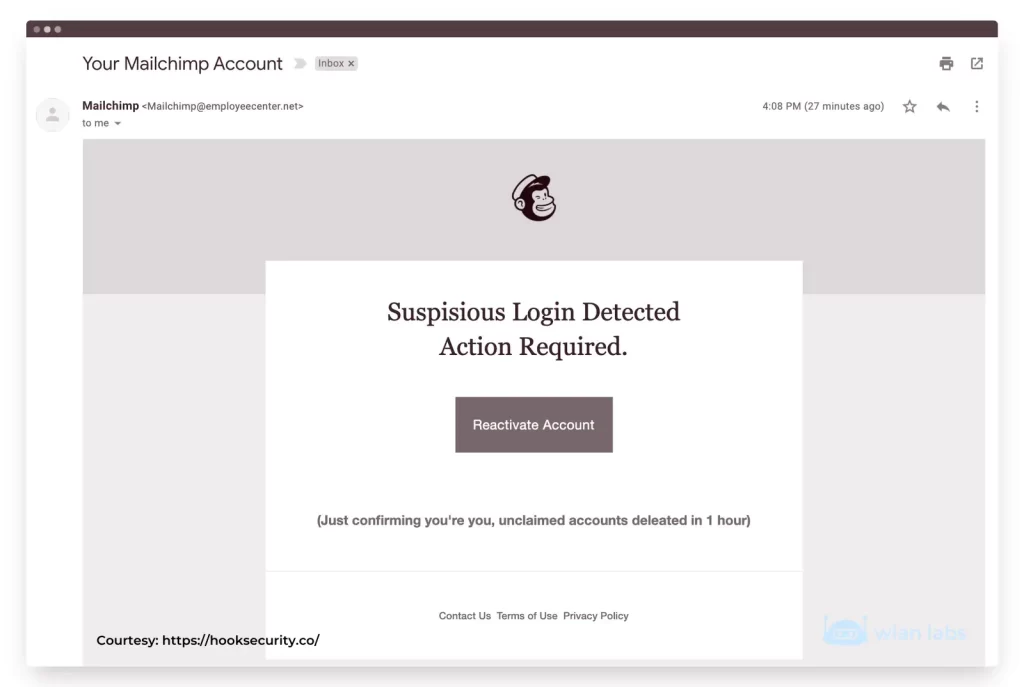
Phishing Example Email 3 (Mailchimp)
How Can We Prevent Phishing Attacks For Good?
When considering how to prevent phishing attacks, individuals and companies need to know how to stop phishing emails in their tracks. Phishing is an attack in which an attacker sends emails pretending to come from someone else, usually a trusted company or individual.
Phishing attacks are often very successful because they are hard for users and security technology to detect. So, how can you protect yourself against them?
Email Filters
Phishing scams are very effective at tricking users into giving up personal information. They often involve sending an email pretending to come from someone you trust, like your bank or credit card company.
These emails usually contain a link that takes you to a website that looks just like the real site but instead sends your details to the attacker.
If you click the link, you could end up handing over your login credentials to a criminal. You should always check the URL of any suspicious email before clicking on a link, and never give out your password to anyone unless you are sure it is genuine.
Email security is important for every organization of any size. There is a lot of information about securing email, but not all are accurate. You need to be sure your email gateway provides the level of protection you need.
A few key points to consider when choosing a gateway are:
- How many users does it support?
- What type of authentication does it provide?

Phishing Style Protection Directly Inside Email Inbox
Cloud-based email security solutions offer a comprehensive solution to this issue. These solutions integrate with email networks via APIs and utilize AI and machine learning to identify malicious emails.
Once identified, they alert you to the threat and allow you to block them from reaching your users. Cloud email security is an essential component of any email infrastructure.
It allows companies to protect themselves from unwanted emails entering their networks while also allowing employees to send messages securely.
Having cloud email security in place means that you have a multilayer approach to stopping phishing attacks. You can use the cloud email security platform alongside the secure email gateway, giving you a layered approach to stopping phishing attempts.
Website Filtrations
Web filtering isn’t just about preventing access to malicious websites; it also helps protect against other attacks.
For example, if you allow users to browse the Internet freely, you might not realize when someone is trying to hack into your network. Web filtering helps keep your company safe by blocking suspicious activity before it happens.
Websites like Google Safe Browsing can help identify dangerous websites, while tools like Cloudflare can help protect your site against attacks.
Website And Email Isolating
Isolation works by creating a sandbox around your browser. Sandboxes are areas within your browser containing certain files and resources.
The site’s code is loaded into the sandbox when you visit a website. Any threats contained within the site’s source code are then isolated from the rest of your system.
Once the page loads, all interactions with the site are also isolated from the rest of the system. This means that if a user clicks on a link, downloads a file, or enters information into a form, the connection to the site is severed immediately after the interaction occurs.
Isolation is a web browser extension that allows you to view all websites through an encrypted tunnel, making them harder to attack.
This removes hackers’ ability to steal your information, such as credit card numbers, passwords, and other personal details.
This is because when you visit a website, your credentials are sent to the server and decrypted before being displayed on the screen. If the hacker could see the decrypted version of the page, he or she could easily copy and paste the credentials onto another site.
For example, if you were trying to log into your bank account, you wouldn’t be able to provide your username and password directly. Instead, you would type them into the login box, which would send them to the server, decrypt them and display them on the screen.
However, if you were using isolation, the credentials would be sent via the encrypted tunnel, meaning there would be no way for the hacker to see what was entered.
Phishing Simulating
Phishing is a type of social engineering attack. Phishers try to trick users into revealing personal information or clicking on links or attachments that lead to malicious websites.
If you’re using a webmail service like Gmail, Yahoo Mail, Outlook, etc., phishing is easy because you will receive all your incoming messages through your browser. You can easily spot suspicious messages by looking for unusual formatting, spelling mistakes, or strange links.
If you think something looks fishy, just hit the back button to go back to the previous page. If you click on any link, even if it’s legitimate, you may end up on a malicious website instead.
Phishing simulations are great tools for testing your security measures. They allow you to test different types of emails, including fake login forms, fake websites, and even fake apps.
These simulations help you determine what information you need to protect against and what type of attacks you should be ready for.
You can create custom simulations using the platform’s built-in libraries of templates. The templates mimic real-life scenarios, such as when an attacker sends a mass mailing to multiple recipients.
Once you’ve selected the template you want to simulate, you can edit the text, images, and links inside the email. You can then preview the changes before sending the email out.
Some simulations can even be customized to mimic different user experiences, like when someone clicks through a link in an email. Admins can simulate phishing emails to individuals, groups, or departments.
They can easily track failed attempts and see trends across the organization. The main benefit of this tool is not to catch out those who struggle with spotting phishing but to help users who struggle to keep themselves safe online.
Phishing targets people, and making sure everyone in the organization is aware of phishing, with ways of receiving training and help to spot them, is an important step in preventing phishing attacks.
Security Awareness Style Training
Phishing exploits human fallibility, not technology. It doesn’t try to bypass your defenses but relies on us making mistakes, using the same password across multiple services, clicking links in messages we aren’t expecting, or failing to notice when someone tries to trick us.
Phishers create realistic-looking websites and emails that mimic trusted sites and institutions like banks, credit card companies, social media platforms, and government agencies. They are designed to fool users into giving away their personal information.
Phishers may even email you pretending to be from your bank if they think you might be careless enough to click through.
How To Prevent Email Phishing Attacks Final Thoughts
The best way to avoid being tricked by phishing scams is to be careful where you get your information. Always check the source of any message you receive. Don’t trust anything you don’t know. And remember: if it seems too good to be true, it probably is!
Contact your financial institution immediately if you suspect a phishing scam has targeted you.
The how to stop phishing email solutions presented here will help protect your users from phishing attacks and reduce their chances of accidentally handing out sensitive information to cybercriminals.
Phishing is a type of social engineering attack that tries to trick an individual into revealing confidential information or transferring money to a fraudulent account.
It can be very damaging when carried out successfully. However, if implemented correctly, it can also be a useful tool for gathering valuable information about your users and your company.
Combining security awareness training with strong technical protections is the best way to secure your organization from phishing attacks.

